Preface
What Is Perforce?
If youâve picked up this book simply because of its riveting title, you may be wondering what Perforce is. Perforce is a software configuration management (SCM) system. SCM systems are used by software developers to keep track of all the software they build and all the components that go into it.
A good SCM system can explain the mysteries of software development and head off its disastersâmysteries like lost bug fixes, and disasters like botched file merges. In large-scale and commercial environments, good SCM is absolutely essential to producing good software.
Perforce, like all SCM systems, keeps track of changes as people do concurrent, parallel work on files. It logs activity, reports who did what; compares, merges, and branches files; and stores files and file configurations. Some of Perforceâs most salient features are:
- The depot
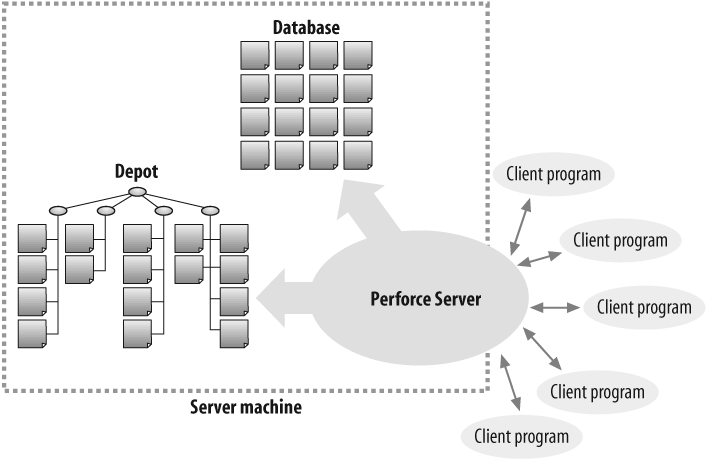
Perforce stores files in a protected repository known as the depot. The depot is a centrally located, permanent archive of all file content submitted by users.[*]
- Workspaces
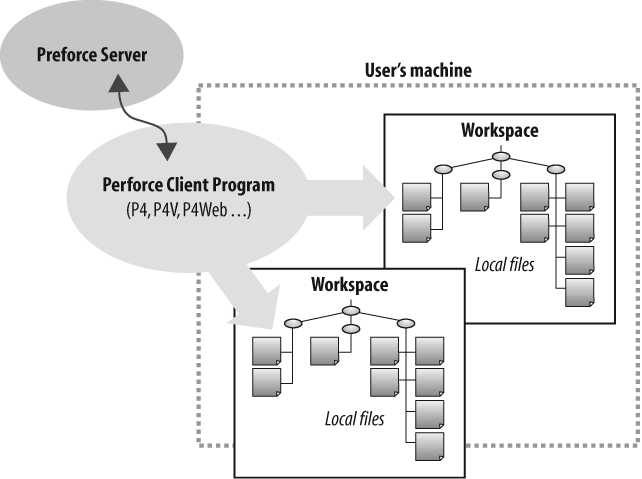
Perforce users work on files in workspaces, private disk areas of their own that contain copies of depot files. In this book weâll describe effective ways developers can use workspaces, and weâll also discuss how workspaces can be used to automate nightly builds, release packaging, web staging, and other software production tasks.
- Changelists
Perforce changelists tie files changed together into single units of work. Every change to the depot can be traced to a changelist, and every changelist marks a known, reproducible state of the depot; the depot evolves as changelists are submitted. In the Perforce view of SCM, it is the changelistânot the file revision, nor the deltaâthat is the atomic transaction of software development. This book will discuss a variety of ways changelists can be used, including treating them as snapshots and using them to identify file dependencies.
- Filespecs and views
The Perforce filespec syntax, and the views that use it, allow selection of files for Perforce operations. Filespecs can define not only the common file collections, like directories, but arbitrary collections of files that constitute codelines, modules, delivery streams, and other containers. They are the key to treating collections of files as versioned objects that can be inspected, rolled back, branched, labeled, compared, and merged at any version.
- Jobs
In Perforce you can record externally defined tasks and statesâbug reports, feature requests, and project milestones, for exampleâin objects it calls jobs. Jobs can be linked to changelists to provide a record of software changes related to tasks. Jobs are also the linchpin of any integration between Perforce and external systems, as weâll see in later chapters.
- Branching
Perforce uses Inter-File Branching to model file variants. In the traditional version tree branching model used by most SCM systems, a file can be be branched and merged only into revisions of itself. In Perforce, any two files can have a branching relationship; branched files are peers, not offshoots, of their originals. A number of chapters in this book are dedicated to describing Perforce branching and its unexpectedly useful applications.
- Integration history
In Perforce, branching and merging are referred to as integration. Perforce records a history of integration events and uses it to direct merges and prevent unnecessary remerging. In this book youâll see how Perforce does that and learn how to anticipate the effect of merges you perform.
- Change tracking
Perforce combines filespecs, changelists, jobs, and integration history to track changes as they are merged from branch to branch. In this book youâll learn how these objects can be used to determine whether a changeâa bug fix, for exampleâmade in one branch has been merged to another, no matter how distantly related.
In addition to these features, which could be considered the interesting capabilities of Perforce, there are also the standard housekeeping and productivity features youâre likely to find in any SCM system, including labels, triggers, change notification, graphical merge tools, file histories, and so forth.
The Perforce System in a Nutshell
Perforce is a client/server system (see Figure P-1). The domain of a Perforce system encompasses a master file repository (the depot), a database, and a constellation of users running client programs. One Perforce Server typically serves an entire Perforce domain. Its job is to communicate with Perforce client programs, analyze and execute user commands, archive and serve up file content, run event triggers, and record system activity in the Perforce database. It also performs a variety of database housekeeping tasks, some on demand and some automatically.
The client component of Perforce, shown in Figure P-2, manages workspace files and communicates with the server. Itâs implemented in a variety of tools designed for users at almost every technical level.
Perforce client tools can be divided roughly into three categories:
- Graphical user interfaces
The Perforce GUIs are the point-and-click client applications. This category includes P4V, P4Win, and P4Web. (The latter is actually more of a plug-in, but because it turns your browser into a Perforce GUI it is marketed as a GUI itself.) Although they donât support every possible Perforce command, the GUIs do support the day-to-day operations of the typical software developer, and they are easy on the eyes. They also provide a variety of data-mining features, including some very nice visualizations of branching and file evolution. For these reasons, even die-hard command-line adherents find them useful. P4V, P4Win, and P4Web can be used interchangeably, although there are some variations in the range of operations they support. All three come with embedded help files that provide rudimentary coaching in how to use Perforce.
- Plug-ins
The Perforce plug-ins category consists of client programs that run behind the scenes, usually on the userâs machine, to enable other applications to work with Perforce. The most widely used is the Perforce SCC Plug-in, which integrates Perforce with Visual Studio .NET. (Thatâs SCC as in Microsoft Source Code Control API; any Windows application that supports the Microsoft SCC API is likely to work just fine with the Perforce SCC Plug-in.)
As Perforceâs popularity grows, plug-ins are emerging that wed less technical applications to Perforce. P4FTP, for example, makes Perforce transparent to people using applications that rely on FTP, and P4Report turns the Perforce database into an ODBC data source for Windows spreadsheet and database tools.
- Programmable clients
The programmable interfaces to Perforce are P4 and P4API. P4, the Perforce Command-Line Client, can be used in interactive shells and in scripts. Itâs the canonical client programâif you canât do it with P4, it canât be done. P4API, the Perforce C/C++ API, is available to embed the client component in applications, scripting languages, and other software. P4 and P4API run on all the operating system platforms Perforce supportsâand there are a lot of themâand they support all Perforce operations, including administrative and privileged operations.
Why Perforce?
The features and capabilities of an SCM system are important, but equally so is its ability to meet expectations and thrive in its habitat. Perforce runs as a self-reliant, self-contained system, and you donât need other software or hardware components installed to use it. Unlike many other SCM systems, Perforce fits into almost any computing environment, thanks to the following features:
- Speed
Perforce is fast. It doesnât make developers wait to check out, check in, compare, or update files, and it doesnât add a processing burden to developersâ machines.
- Centralized repository
In the Perforce system, there is one centralized repository per domain for files and SCM data. Very large companies may have several Perforce domains, but thatâs typically an organizational choice, not a limitation of domain size. (Perforce domains at some large companies are known to encompass over 1,000 users each.) While it may be argued that a centralized repository puts your SCM system at risk of a single point of failure, that risk is vastly outweighed by several advantages. First, you have only one machine per domain to take care of to protect your assets. Second, you donât have to worry about where your assets are. Office moves and machine upgrades donât perturb your central SCM repository. And third, as long as your central SCM server is running, all your users have access to it. The failure of one machine doesnât impede SCM access for users elsewhere else in your system.
- No external database required
Some SCM systems require you to configure and administer an external database system like SQL Server or MySQL. Perforce provides its own database. When you install Perforce, youâre installing a reliable, self-contained database, customized for Perforce SCM.
Because the Perforce database canât be accessed by any other means than the Perforce Server, thereâs not much that can go wrong. It does require that the system administrator schedule regular checkpoints and backups, but other than that, very little hands-on administration is required. Database recovery performed after a disk failure or other misfortune can be done manually by the system administrator or through automated tools. Perforce provides tools for checkpointing, recovery, and for automatically upgrading the database when a new release is installed.
- No reliance on networked file sharing
Some SCM tools rely on networked file sharing (NFS) of one kind or another. NFS is not an ideal solution for SCM; network file sharing can be slow, and makes it difficult for the SCM tool to handle file format differences. (Have you ever opened up a file in Notebook only to see all its lines running together? Or opened up a file in vi and seen
^Mcharacters at the end of every line?) NFS is also very machine-dependent; clock synchronization and other interoperability issues make version control difficult.Perforce does not use NFS. Instead, it does its own file transport using TCP/IP. This gives it control over the files it cares about and, because TCP/IP is so universally supported, makes it capable of running on more operating system platforms.
- No HTTP server required
Some SCM systems require you to configure an HTTP server, like Apache or IIS, to perform the duties of an SCM server. Perforce provides its own server and runs independently of your web servers.
Traditionally, software development organizations were formed of developers working together at the same company, at the same location. Most SCM systems, including Perforce, are suited for that kind of organization. But Perforce has built-in features that make it suitable for nontraditional teams, including teams formed of developers who work outside of the office, developers who work in separate divisions, and even developers who work for completely different companies:
- Process impartiality
Perforce imposes almost no built-in workflow or process rules. Itâs designed with certain software development activities in mind (all of which will be discussed in later chapters), but it can accommodate almost any procedure or methodology. Any workflow or process you have established (or that you would like to establish) can be automated with Perforce.
- File types
While some SCM systems have restrictions on handling certain file types, Perforce can store and manage text files, binary files, Unicode files, native Apple files on the Macintosh, Mac resource forks, and Unix symlinks in its repository.
- Product distribution and vendor drops
The Perforce Server can access file repositories in other Perforce domains. This makes a seamless, Perfore-to-Perforce distribution of software products possible. In other words, you can distribute your product directly from your Perforce repository to other organizations, as long as they have Perforce, too. And you can receive vendor drops from other organizations directly from their Perforce repositories. In fact, you can even branch or merge files from their repositories directly into yours. All the while, a history of what youâve released and received is being collected and recorded in your SCM database.
- Firewalls and tunnels
As mentioned, Perforce uses TCP/IP to communicate between its components. The firewall that prevents external access to machines inside your network also prevents access to your Perforce repository. However, that doesnât mean that all your developers have to be inside your firewall. Perforce can be used in a Virtual Private Network (VPN), when one has been created, and authorized users can use Secure Shell (SSH) to tunnel through a firewall with Perforce commands. The advantage here is that you can extend your SCMâand hence your software development projectsâto participants all over the world without having to give them direct access to your machines or intranet.
For a commercial product, Perforce is unusually accessible. Many new users are lured to Perforce simply because itâs so much easier to get started with it than it is with any other SCM system:
- Easy to install
Unlike open source software, which generally has to be configured and built, Perforce tools are executable out of the box. By comparison, CVS and Subversion may be free, but they arenât free of the problems of building open source software. If youâve ever been down the rabbit hole of trying to find, configure, compile, and install all the components in the dependency chain of an open source tool, youâll appreciate the simplicity of getting Perforce up and running. Itâs literally a 10-minute job: you download a couple of binary files, run one to start up a server, and run the other as your client-side interface to it.
- Runs everywhere
Perforce runs on a huge variety of operating system platforms. Your laptop, the fully loaded machine at your office, the discount PC in your childâs room, the old VAX you found on the sidewalk on trash collection day, even the ground-breaking new operating system youâre developingâchances are very good that thereâs a version of Perforce that runs on it.[*] Since its inception, Perforce Software has made a point of porting its tools to as many platforms as possible. Thatâs been relatively easy to do, because the core components of Perforce are small, standalone programs. And to this day, every version of Perforce ever released can be downloaded for freeâin prebuilt, executable form, no lessâfrom the Perforce FTP site.
- Costs nothing to try
You can download all Perforce software and documentation for free, without having to talk to a sales rep or even fill out a form on the Web. The software you download is fully functional; itâs the vendorâs intent that you try Perforce and really see if it meets your needs before you commit to buying it. If you want to test-drive Perforce in an environment with more that two users, Perforce Software will give you a limited-term license for as many users as you need. So instead of spending time in meetings arguing with everyone else about whether Perforce will meet your needs, you and your colleagues can spend time actually trying it out.
- Easy budget planning
Itâs easy to plan a budget for Perforce. How many developers will you have? Thatâs what youâll be paying for. Perforce is priced per user, regardless of what theyâre doing and the environments in which theyâre working.
- All-inclusive pricing
Once youâve paid or Perforce, you can download and run as many server programs as you need, on as many operating systems as you have, as long as you donât exceed the number of users youâve paid for. You can run your servers anywhere in the world, and any of your users can use any of your servers. (If you allow them to.) The price you pay includes all of the Perforce client programs, plug-ins, and tools.
- Free to students, hermits, and saints
In fact, if youâre going to use Perforce for educational purposesâyouâre teaching a programming class, or developing software for a school project, for exampleâthe vendor will provide you with a free license to cover as many users as are involved. Just contact Perforce Software and let them know about your project. You need a license, by the way, only if you have more than two users accessing your Perforce repository. That means that if youâre working on a software development project all on your own, or with just one other person, you can use Perforce for free, forever. And if you are one of the saints developing open source software for no remuneration, you can get a free Perforce license to cover you and everyone else working on your project.
About This Book
This book is written with a particular reader in mind. The reader is familiar with SCM in general, and is most likely a programmer, a project manager, or a build engineer involved with software development. This book is written especially for the reader who wears more than one of those hats on the job and is responsible for some or all of the interconnection between the roles they represent. If youâre pursuing better ways to keep it all connected, and are interested in seeing how Perforce fits in, this book is for you.
One purpose of this book is to present Perforceâs potential as a software configuration management tool. This is a strictly academic purposeâyou need not be a Perforce user to gain insight from it. Anyone interested in comparative SCM will find worthwhile material in this book.
The second purpose of this book is to help Perforce users understand why Perforce works the way it does. Most users come to this level of understanding on their own eventually; it is the level of understanding that prompts them to post âAha!â messages to online Perforce discussions. It is also the level of understanding also makes the difference between simply using Perforce to do what any SCM system can do and exploiting Perforce to accomplish what other systems canât. This book will get you to that level sooner.
There are two parts to this book:
Part I (Chapters 1â5) describes Perforce commands and concepts. Itâs not a tutorial, nor is it a referenceâitâs more of a whirlwind technical tour. It will provide you with a baseline knowledge about fundamental Perforce operations.
Part II (Chapters 6â11) describes the big picture, using Perforce in a collaborative software development environment. It outlines recommended best practices and shows how to implement them with the Perforce operations you were introducted to in Part I.
Whatâs Not In This Book
This book contains no tutorials, no hands-on exercises, and no getting-started guides. Although it does contain numerous examples of basic and advanced commands, this book is not meant to be a primary source of instruction for new Perforce users. The role of this book is to complement the existing product manuals with tips and ideas for using Perforce to its full advantage.
This book doesnât document actual case studies. Itâs almost impossible to describe actual case studies without detail-laden examples that put a reader right to sleep. So weâve foresaken realism on the principle that simple, readable examples can be extrapolated to complicated, real-world solutions more easily than simple solutions can be inferred from painstakingly realistic examples.
This book wonât address industry standards, benchmarks, or certification models, although it will surely be of use to practioners of such standards. Perforceâs strength is in its versatility and accessibility. It makes a robust foundation for a compliance process, but it does not itself enforce compliance.
This book is rather light on system administration issues. Perforce is a tool you can use to great effect without knowing anything about installation, security, backups, upgrades, migration, and performance. When you do need to know about these things, youâll find the Perforce manuals and other materials that are readily available at the Perforce Software web site to be a rich resource.
This book doesnât start with a chapter explaining SCM. There was a time when SCM was arcane and indistinct, but those days are gone, and the world now abounds with books and web sites designed to bring novices up to speed.
Additional Reading
Software configuration management, as a topic, is finally conquering measurable shelf space in the computer section of bookstores. A number of SCM issues and challenges have been fully explored by other writers, and this book wonât retread that ground. If youâre a complete SCM novice you might want to take a look at some of the introductory or complementary titles available, including:
- Real World Software Configuration Management by Sean Kenefick(APress)
If software configuration management is in your job description, this book is for you. Itâs a no-nonsense explanation of SCM best practices with down-to-earth advice about getting going and sticking with them.
- Software Configuration Management Patterns: Effective Teamwork, Practical Integration, by Steve Berczuk with Brad Appleton(Addsion Wesley)
This is a concept book that manages to be quite practical nevertheless. Its detailed analyses of SCM problems and solutions are for the most part independent of any particular SCM system. It also offers a comprehensive comparison of the terminology used by contemporary SCM systems.
- Configuration Management: The Missing Link in Web Engineering, by Susan Dart(Artech)
This wide-ranging survey of risk management and return on investment includes brief case studies of a variety of SCM systems in use.
- Open Source Development with CVS, by Karl Fogel and Moshe Bar(Paraglyph)
This very readable book combines a detailed guide to using CVS with an interesting discussion of its history and its application in open source projects. Itâs a good source of insight into how todayâs SCM terminology and usage conventions have evolved from their earliest progenitors.
- Software Configuration Management Strategies and Rational ClearCase, by Brian A. White(Addison Wesley)
With its in-depth coverage of the ClearCase view of problems and solutions, this book presents an interesting contrast to SCM with Perforce.
- The Pragmatic Programmer, by Andrew Hunt and David Thomas(Addison Wesley)
Not about SCM per se, this book touches on many software development practices that harmonize with good SCM.
Finally, while this book will teach you about Perforce, it wonât teach you about all the Perforce commands, command forms, and command options available to you. For that level of detail, go to the Perforce web site and look for the following product manuals:
- The Perforce Command Reference
An A-to-Z reference to P4 commands. You may wish to bookmark this manual and refer to it to find out more aboutâor alternatives toâthe command forms and options shown in Practical Perforce.
- The P4 Userâs Guide
A detailed guide to using Perforce for working with files. This manual is geared toward end-users and uses P4 commands in its examples. Consult this manual for in-depth information about the Perforce user environment and a variety of typical developer tasks.
- The Perforce System Administratorâs Guide
A detailed guide to setting up a Perforce Server and managing a Perforce system. Consult this manual for in-depth information on backups, security, triggers, scripting, job customization, review daemons, performance, and OS-specific issues.
The online versions of these and other Perforce product manuals are available free at http://www.perforce.com/perforce/technical.html. You can also buy bound, hard copy versions of the same manuals; check the web site for details.
Conventions Used in This Book
This book uses the following typographic conventions:
Constant widthis used for names of commands, command fragments, and command options.Italic is used for filenames and for characters used in the context of file identifiers.
Button labels in graphical application windows are shown in regular text, and are often intercapped.
Menu â Item â Item represents sequential selections in graphical application menus.
Examples that show commands as they are typed, but that do not show command output, look like this:
type this commandExamples that show commands as they are typed, and that show command output as well, look like this:
type this commandand you will see output that looks like thisExamples that show the contents of files and scripts look like this:
these are lines that appear in a file
Examples of Perforce spec forms look like this:
Field1 value1 Field2 value2
In addition, the following formats are used to grab your attention and relieve the tedium of what could otherwise be monotonous reading:
Using Code Examples
This book is here to help you get your job done. In general, you may use the code in this book in your programs and documentation. You do not need to contact us for permission unless youâre reproducing a significant portion of the code. For example, writing a program that uses several chunks of code from this book does not require permission. Selling or distributing a CD-ROM of examples from OâReilly books does require permission. Answering a question by citing this book and quoting example code does not require permission. Incorporating a significant amount of example code from this book into your productâs documentation does require permission.
We appreciate, but do not require, attribution. An attribution usually includes the title, author, publisher, and ISBN. For example: "Practical Perforce, by Laura Wingerd. Copyright © 2006 OâReilly Media, Inc., 0-596-10185-6.â
If you feel that your use of code examples falls outside fair use or the permission given here, feel free to contact us at permissions@oreilly.com.
Safari® Enabled
When you see a Safari® Enabled icon on the cover of your favorite technology book, that means the book is available online through the OâReilly Network Safari Bookshelf.
Safari offers a solution thatâs better than e-books. Itâs a virtual library that lets you easily search thousands of top tech books, cut and paste code samples, download chapters, and find quick answers when you need the most accurate, current information. Try it for free at http://safari.oreilly.com.
How to Contact Us
We have tested and verified the information in this book to the best of our ability, but you may find that features have changed or that we have made mistakes. If so, please notify us by writing to:
| OâReilly Media, Inc. |
| 1005 Gravenstein Highway North |
| Sebastopol, CA 95472 |
| (800) 998-9938 (in the United States or Canada) |
| (707) 829-0515 (international or local) |
| (707) 829-0104 (FAX) |
You can also send messages electronically. To be put on the mailing list or request a catalog, send email to:
| info@oreilly.com |
To ask technical questions or comment on the book, send email to:
| bookquestions@oreilly.com |
We have a web site for this book, where you can find examples and errata (previously reported errors and corrections are available for public view there). You can access this page at:
http://www.oreilly.com/catalog/practicalperforce
|
Acknowledgements
Practical Perforce couldnât have been written without the participation and encouragement of many people. I thank Christopher Seiwald, creator of Perforce the product and Perforce the company, for seeing the value in this project from its outset. I thank Kathy Baldanza for coaxing early drafts out of me and asking painful questions like âHowâs that book coming?â I thank everyone who reviewed the drafts (especially Jason Kao!) for catching so many of my dumb mistakes. I thank Jonathan Gennick at OâReilly for making the endgame painless. And I thank Chris Comparini for making many hours spent sitting with a laptop a pleasant and companionable experience.
Above all, I thank the many peopleâusers, customers, consultants, colleagues, and friendsâwho have indulged my compulsion to talkâat trade shows, at conferences, at the office, and at partiesâabout how SCM works in general and how Perforce pays off in particular. Their stories, their diagrams, and their sharp insights have shaped my ideas. They are the âweâ in this book, the voice that narrates the knowledge Iâve tried to impart.
[*] The data format of the Perforce depot is not proprietary; it is, in fact, consistent with the RCS archive format. Because of this, there is a common misperception that Perforce is an RCS wrapper. Itâs not.
[*] The Perforce web site used to boast that âIf the client program doesnât run on your platform, weâll port it there.â Paradoxically, while compatibility with exotic, leading-edge platforms gave Perforce a foot up in the SCM market, the market itself has become more homogeneous. Today, established Windows and Linux operating systems seem to be the preferred platforms for even the newest software technology projects.
Get Practical Perforce now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.