A cloud- and fog-enabled IoT system has many points of interconnection, and many services running in support of system operations and management. Each of these represent potential entry points into the system for malicious actors.
With the addition of new edge-based services from CSPs, attackers can also focus on the execution logic on the device itself to cause malfunctions or deny operations. The addition of a fog layer adds more complexity to the system and another set of attack targets:
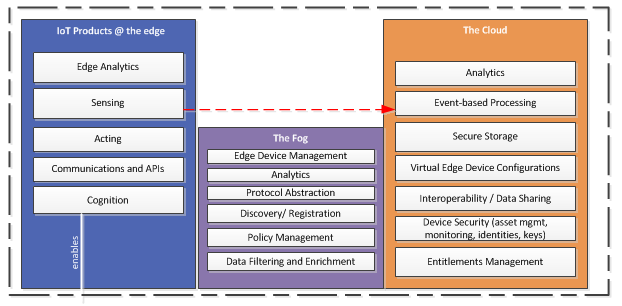
The following table examines some of the threats that may be associated with a cloud-enabled IoT system. For each, ensure ...

