Identifying the attack surface
This section is one of the most interesting sections when working with Drozer. We can identify the attack surface of our target application with a single command. It gives the details such as exported applications components, if the app is debuggable, and so on.
Let's go ahead and find out the attack surface of testapp.apk. The following command is the syntax for finding the attack surface of a specific package:
dz> run app.package.attacksurface [package name]
In our case for testapp.apk, the command becomes as follows:
dz> run app.package.attacksurface com.isi.testapp
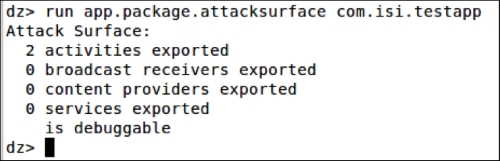
As we can see in the previous screenshot, the testapp ...
Get Penetration Testing: A Survival Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

