Spear-phishing attack
This module allows you to create customized e-mails to target specific victims. The aim of this module is to integrate a payload into the attachment and send it across to the victim via a spoofed e-mail.
You need to select the second option, that is Create a FileFormat Payload, which will guide you to select a specific file format to exploit. The entire menu is easy to follow and self-explanatory:
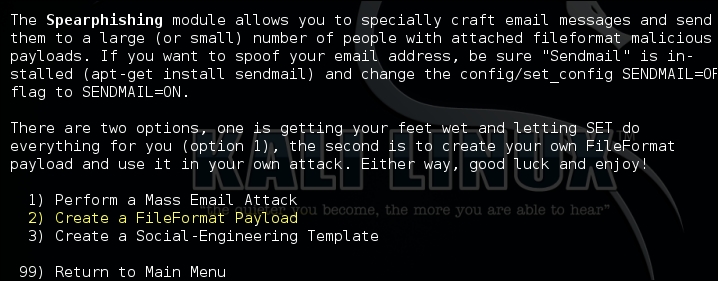
Next, select a specific payload that you want to use; it will prompt you to select the type of command shell that you want to execute when the victim machine is successfully exploited. The reverse TCP shell and meterpreter reverse TCP ...
Get Penetration Testing: A Survival Guide now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

