Chapter 3. Implementing security on the PDA management environment 85
– policy_server_port
Is the port used for SSL communication with the Policy Server. The default
is port 7135.
– authorization_server_port
Is the port used for SSL communication with the Authorization Server. The
default port is 7136.
– configuration_file
Is the URL to the configuration file. The URL must use the file:/// format.
The default is <java_home>/PdPerm.properties, where <java_home> is the
directory where the Access Manager Java Runtime Environment is
installed.
– keystore_file
Is the URL to the keystore file. The URL must use the file:/// format. The
default is <java_home>/PdPerm.ks, where <java_home> is the directory
where the Access Manager Java Runtime Environment is installed.
The PDPerm.properties and PdPerm.ks files must be in the same
directory.
– operation
Specify create. Valid operations are create, replace, or unconfig.
For example:
java com.tivoli.mts.SvrSslCfg twg_application secmastpw itcmpda3 itcmpda3
7135 7136
file:///C:/WebSphere/AppServer/java/jre/PolicyDirector/PdPerm.properties
file:///C:/WebSphere/AppServer/java/jre/PolicyDirector/Pd.ks create
3.3 Configuring the secure environment
This section provides configuration procedures for enabling security in the
pervasive devices management environment. Such procedures will enable the
integration of IBM Tivoli Access Manager with Tivoli Web Gateway.
We describe administrative and configuration tasks on both the IBM Tivoli
Configuration Manager/Tivoli Web Gateway and the Access Manager servers.
For easier understanding, we describe whether the task should be performed on
the Access Manager server or the IBM Tivoli Configuration Manager/Tivoli Web
Gateway server
86 PDA Management with IBM Tivoli Configuration Manager
3.3.1 Creating a WebSEAL junction to the Web Gateway
Access Manager provides authentication, authorization, and management
services for a network. In our environment, these services are provided by the
front-end WebSEAL Servers that integrate and protect Web resources and
applications located on back-end Web application servers. The back-end Web
application server in our scenario is represented by the Tivoli Web Gateway
system.
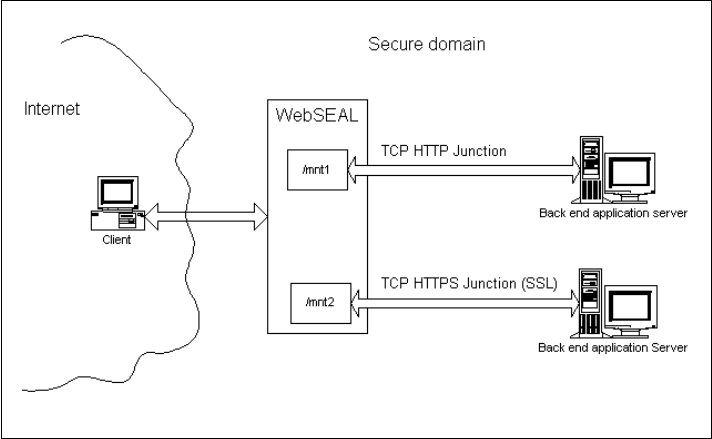
The connection between a WebSEAL Server and a back-end Web application
server is known as a WebSEAL junction, or junction. A WebSEAL junction is a
TCP/IP connection between a front-end WebSEAL Server and a back-end Web
application server. Junctions allow WebSEAL to protect Web resources located
on back-end servers.
A WebSEAL junction over a TCP connection provides the basic properties of a
junction but does not provide secure communication across the junction. SSL
junctions allow secure end-to-end browser-to-application transactions. You can
use SSL to secure communications from the client to WebSEAL and from
WebSEAL to the back-end server. The back-end server must be HTTPS-enabled
when you use an SSL junction. Figure 3-26 represents the two basic types of
junction.
Figure 3-26 Basic types of WebSEAL junctions

Chapter 3. Implementing security on the PDA management environment 87
More information on junctions can be found in the
IBM WebSEAL Administration
Guide
, SC32-1134.
WebSEAL supports the following authentication methods:
Basic Authentication (ba-auth)
Basic authentication is a standard method for providing a user name and
password to the authentication mechanism. BA is defined by the HTTP
protocol and can be implemented over HTTP and over HTTPS. By default,
WebSEAL is configured for authentication over HTTPS via basic
authentication.
Forms-based Authentication (forms-auth)
Access Manager provides forms-based authentication as an alternative to the
standard basic authentication mechanism. This method produces a custom
HTML login form from Access Manager instead of the standard login prompt
resulting from a basic authentication challenge. When you use forms-based
login, the browser does not cache the user name and password information
as it does in basic authentication. This method can be implemented over
HTTP and over HTTPS as well.
Both base and forms authentication settings are done in the WebSEALd.conf file
located in the C:\Tivoli\PDWeb\etc directory.
Also in the WebSEALd.conf file there is the use-same-session entry. This option
is for enabling or disabling the ability to use the same session data when a client
switches between HTTP and HTTPS.
More information on authentication can be found in the
IBM WebSEAL
Administration Guide
, SC32-1134.
in order to create a junction between the Access Manager WebSEAL Server and
the Tivoli Web Gateway Server,
on the Access Manager machine, perform the
following steps:
1. Start the pdadmin command environment by clicking Start -> Programs ->
Access Manager for e-business -> Administration Command Prompt.
2. Log in to the Access Manager by entering the command:
login -a sec_master -p sec_master_password
Note: If the forms-based authentication method is enabled, the basic
authentication method settings are ignored.
Handheld devices can only use basic authentication.
Get PDA Management with IBM Tivoli Configuration Manager now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

