Chapter 4. Runtime patterns 65
Improves reuse.
Addresses any technical and information model discrepancies amongst
services.
Provides a single configuration point for distributed deployment.
Decouples service requesters from providers
Provides a common access point for service requesters
Provides centralized security for services
The ESB can span across multiple system/application tiers, and may extend
beyond the enterprise boundary.
Note that this Runtime pattern appears to be identical to the SOA profile of the
Runtime pattern for the Directly Integrated Single Channel application pattern.
The use of SOA and an ESB introduces the flexibility to accommodate a wide
range of functionality, including point-to-point, routing, and as we will see later,
decomposition capability.
4.4 Runtime patterns for Decomposition
The Decomposition application pattern expands on the Router application
pattern, providing all the features and functions of that pattern and adding
recomposition/decomposition. This capability allows an incoming request to be
split into multiple requests directed to separate back-end applications. The
results of these requests is recombined into a single response to the user.
The Runtime pattern for the Decomposition application pattern has been broken
down into a generic Runtime pattern and then further refined using an SOA
profile.
4.4.1 Generic Runtime pattern for Decomposition
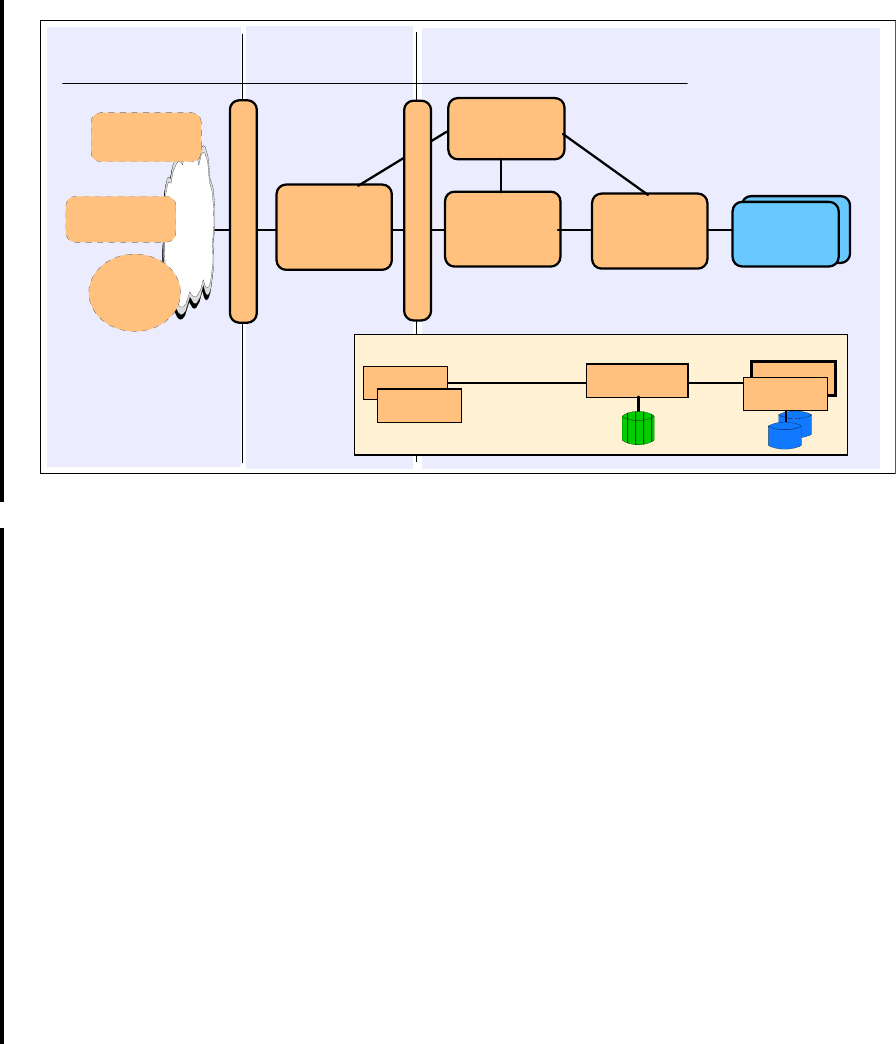
The Runtime pattern shown in Figure 4-6 on page 66 represents one solution for
the Decomposition application pattern.
66 Patterns: Implementing Self-Service in an SOA Environment
Figure 4-6 Decomposition application pattern::Generic runtime pattern
In the Decomposition application pattern, the decomposition tier serves as an
integration point for delivery channels in the presentation tier, allowing access to
individual back-end applications. In the Generic runtime pattern (Figure 4-6 on
page 66), the functions of the decomposition tier are performed by an integration
server node. The functions of the presentation tier are performed jointly by a
Web server redirector node and the application server node. Placing a Web
server redirector in the DMZ provides an extra layer of security by putting all
application logic behind the firewall. Only a portion of the presentation function is
left in the DMZ.
The Web server redirector serves static HTTP pages, while forwarding dynamic
servlet and JSP requests to the application server. The presentation logic,
therefore, spans both nodes. Together, these two provide the presentation tier,
capable of handling multiple, diverse presentation styles. Using a redirector
allows you to place the bulk of the business logic behind the protection of both
the protocol and domain firewalls.
In addition to presentation logic (for example, JSPs), the application server
contains some business logic. This is primarily in the form of the controlling
servlets required to access the back-end applications. The application server
builds a request based on user input and passes it to the integration server node.
The primary business logic resides in the back-end applications.
Internal Network
Demilitarized Zone
(DMZ)
Outside World
Protocol
Firewall
I
N
T
E
R
N
E
T
Public Key
Infrastructure
User
Web
Server
Redirector
Domain Name
Server
Directory and
Security
Services
Application
Server
Presentation
Decomposition application pattern
Application
Application
Decomposition
Integration
Server
Existing
Applications
and Data
Domain
Firewall
Presentation
Get Patterns: Implementing Self-Service in an SOA Environment now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

