Useful Operating System Commands
The following section provides a number of useful operating system functions that can be used to investigate security components.
The first method involves seeing what ports are being used within the operating system. The following example shows all the processes listening on the Linux environment that I used to write this book. You can use the same command in a Windows environment to show the ports being used.
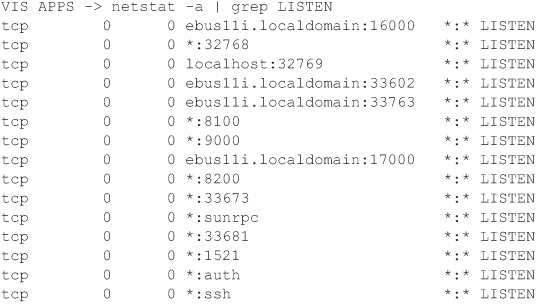
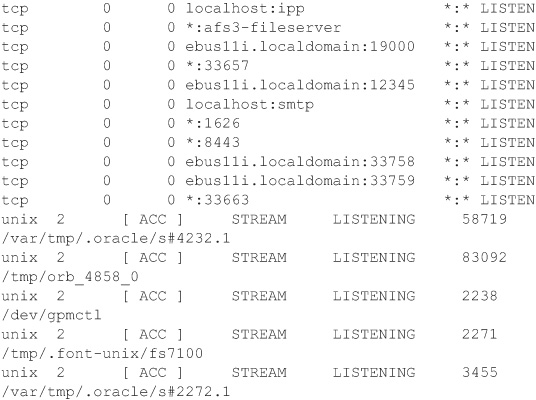
You can validate the Unix password profiles using the default login.defs file. I have copied the security ...
Get Oracle E-Business Suite Security now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

