To ensure security throughout your IT environment, you have to decide how you are going to deploy the components of the overall environment. This section covers some of the considerations you need to keep in mind when implementing a secure deployment of Oracle Application Server 10g, including the use of DMZs, the delegation of security privileges, and the use of Oracle Enterprise Manager 10g to manage security.
Oracle Application Server 10g enables deployment using a DMZ topology. In the context of computer networking, a DMZ is a server placed between two firewalls and thus separated from the Internet and intranet(s). Its placement means that the server exists in a secure buffer zone.
Tip
The word DMZ comes from a military term referring to a "demilitarized zone.” DMZ was a term used during the Korean War to indicate a no-man’s land where troops residing in North Korea and South Korea were not allowed to enter. The DMZ was a zone of security created to prevent attacks or incursions from either side.
In one typical deployment, you might want to use a DMZ to separate an OracleAS Portal repository database from the database containing business data. The DMZ prevents a hacker from gaining access to the OracleAS Portal password in Oracle Application Server and then using the OracleAS Portal’s DBA privileges to wreak havoc on corporate data. In another typical deployment, you might use the DMZ topology for intrusion containment.
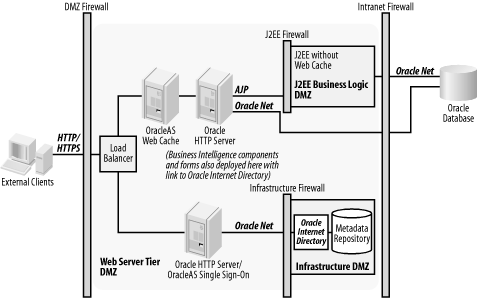
Figure 4-2 shows a typical DMZ deployment in an Oracle Application Server environment.
For details about DMZ deployment strategies, see the Oracle Application Server 10g Security Guide, a part of the standard Oracle Application Server documentation set. (That manual, and many others, are referenced in the Appendix.) In that guide, Oracle provides the following recommendations:
Make sure that all OracleAS Web Cache, HTTP servers, OracleAS Single Sign-On HTTP servers, HTTP load balancers, and HTTPS-to-HTTP appliances reside in the DMZ.
If direct Oracle Internet Directory access is needed from the Internet, place the Oracle Internet Directory servers in the DMZ.
Don’t allow J2EE servers to be directly accessible to the intranet. (Instead, place business logic behind a J2EE firewall.)
Place databases containing metadata and the Oracle Internet Directory database behind a firewall in an infrastructure DMZ.
Deploy OracleAS Portal on a single HTTP server with OC4J within the web server tier’s DMZ; you can also deploy OracleAS Discoverer, OracleAS Reports Services, and OracleAS Forms Services behind an OC4J firewall.
An Oracle Internet Directory infrastructure may be shared by administrators of applications in different business areas or with different responsibilities. A delegation model provided in Oracle Application Server enables the delegation of appropriate levels of privileges within a shared infrastructure.
Delegation is structured as follows:
The Oracle Internet Directory super user
orcladmincreates an identity management realm, identifies the realm administrator, and delegates all privileges to the realm administrator.The realm administrator delegates roles for managing Oracle components and grants privileges associated with those roles.
The context administrators, in turn, delegate Oracle Application Server roles.
Oracle Application Server user roles include installation administration, application administration, identity management infrastructure administration, and Oracle Application Server application users.
Oracle Enterprise Manager 10g provides a single interface for managing multiple Oracle Application Servers through the Application Server Control tool installed for each application server being monitored. We discussed Oracle Enterprise Manager 10g, Application Server Control, and other system management tools in more detail in Chapter 3.
You can use Application Server Control for a number of different security management activities. For example, through Application Server Control you can configure application security resources, including JAAS provider services. You can also configure and modify the Oracle Internet Directory and OracleAS Single Sign-On. You can use the Application Server Control Infrastructure page to change infrastructure services if you change the Oracle HTTP Server OracleAS Single Sign-On port number on an identity management installation, the Oracle Internet Directory port number (non-SSL or SSL), the Oracle Internet Directory Mode (dual-mode or SSL), or the host on which Oracle Identity Management or the OracleAS Metadata Repository resides. If you do this, you must perform a variety of manual command-line tasks to prepare the new infrastructure services before using Application Server Control to make the change (those tasks are described in the Oracle Application Server 10g Administrator’s Guide ).
Get Oracle Application Server 10g Essentials now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.