VPN and Remote Access Module
As the name implies, the primary objective of this module is three-fold: terminate the VPN traffic from remote users, provide a hub for terminating VPN traffic from remote sites, and terminate traditional dial-in users. All the traffic forwarded to the edge distribution is from remote corporate users that are authenticated in some fashion before being allowed through the firewall.
Figure B-21. Remote Access VPN Module Traffic Flow
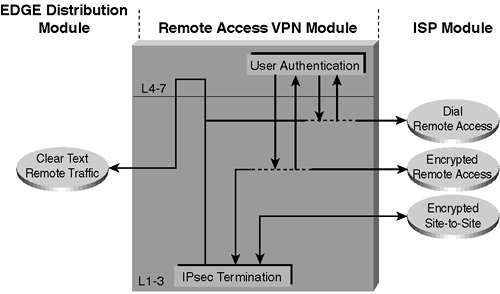
Key Devices
VPN Concentrator— authenticate individual remote users using Extended Authentication (XAUTH) and terminate their IPsec tunnels
VPN router— authenticate trusted remote sites and ...
Get Network Security Principles and Practices now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

