Similar checks can be performed using the Metasploit modules. Open Kali Linux, which we installed in the VM, and type the following command in Terminal:
msfconsole
This is used to open the Metasploit console. There is also a GUI version of Metasploit available with the name Armitage. To find out the various Metasploit modules that are available for SCADA, enter the following command:
searchscada
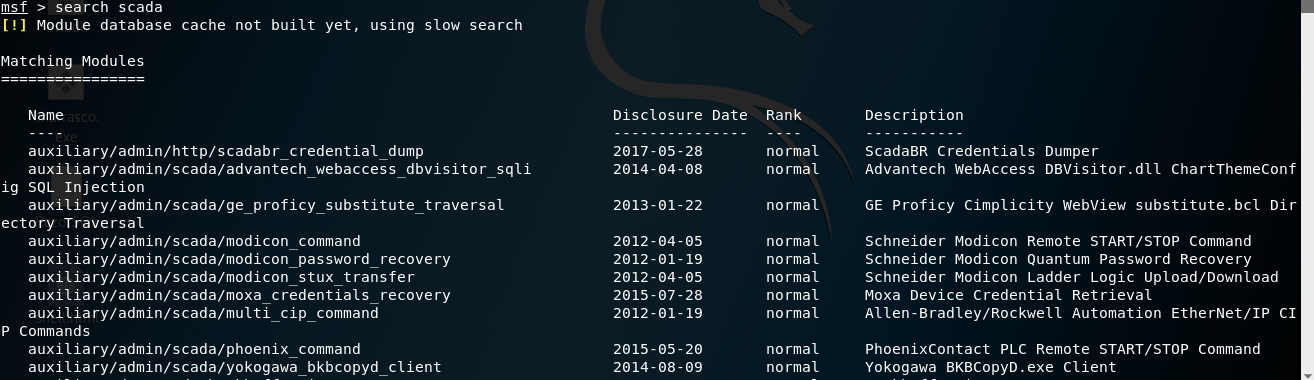
As shown in the preceding screenshot, various modules for SCADA that are supported by Metasploit are loaded. Let's try a specific search ...

