3.6. We're Watching You
After you allow users and machines onto the network, you need to ensure that they remain in compliance with the policies that they passed in order to get on the network.
|
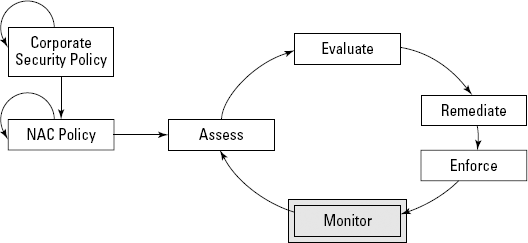
The final phase — monitoring — comes into play when you want to make sure that everyone stays compliant.
When NAC monitors your network, it continually watches users and endpoints for updates or changes in their compliance status, as shown in Figure 3-6.
If a user switches off his or her personal firewall or antivirus application, your NAC system should be able to detect that change and react accordingly.
Perhaps your operating-system vendor just rolled out a very high severity patch that corrects a gaping security hole. Your NAC system should allow you to roll out a policy that scans for that patch after IT pushes it to all the managed systems so that you can ensure everyone has accepted and installed the patch.
Figure 3.6. Monitoring your NAC solution.
You can choose ...
Get Network Access Control For Dummies® now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

