3.3. Putting the Pieces Together
During the assessment phase (discussed in the preceding sections), you collect a lot of information about the user, his or her machine, and the environmental factors associated with the access request. The next step in the NAC lifecycle, indicated by the shaded area in Figure 3-3, is evaluation. In this phase, your NAC system puts together all the pieces of information collected during the assessment phase.
Figure 3.3. The evaluation phase.
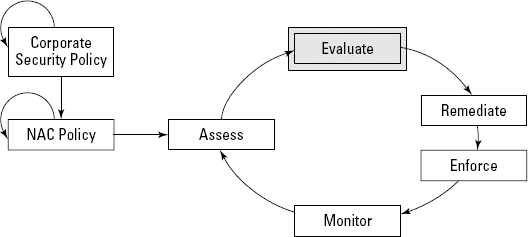
Most NAC deployments have different sets of policies related to different groups of users. In the evaluation phase, the NAC system examines the tens, hundreds, or thousands of new session requests coming onto the network and determines exactly which policy should apply to which request.
For example, your NAC system performs user authentication, but at the same time, it pulls from your corporate directory any additional required information related to that user. Your corporate directory might include group membership information, which indicates what groups the user is a member of in the organization, allowing NAC to automatically differentiate employees from contractors or members of the Finance department from members of the Engineering department.
NAC uses this information to determine which, of potentially many, policies apply to a particular authentication request. It then evaluates the next steps required ...
Get Network Access Control For Dummies® now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

