3.4. Not So Fast...
Remediation, shown in Figure 3-4, is an optional step in the NAC process.
Some users might never go through remediation if their machines stay in compliance with policies at all times. For example, your desktop deployment group might have a very firm handle on software distributions and can manage to keep all the employee machines on the network patched and up to date. When a user comes onto the network with such a machine, NAC can bypass the entire remediation step, moving right on to enforcement, which you can read about in the following section.
Figure 3.4. The remediation stage.
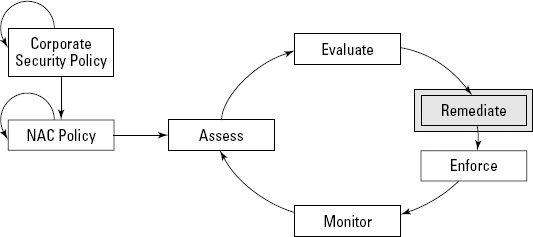
Remediation is an incredibly important part of the NAC lifecycle. In this step, your NAC system gets any machine compliance issues corrected so that the user gets full access to any resources for which he or she is authorized. Properly chosen and deployed remediation can make the difference between a safe and secure network, and a horrible situation where machines are out of compliance and your helpdesk is flooded with calls from frantic users.
NOTE
You ultimately want to get all your users onto the corporate network with full access to everything that their roles imply they should be able to access. Nobody wants to be the person keeping the CEO from her e-mail simply because her antivirus program is out of date. If users can't get their work done, they either try to circumvent ...
Get Network Access Control For Dummies® now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

