3.5. Let Me In!
After collecting all the information related to a new session request, correcting any deficiencies, evaluating all your policies alongside this collected information, and figuring out exactly which resources your end user can access, the NAC system now needs to enforce those policies.
|
After the NAC system determines the level of access that an end user can have, enforcement becomes the next hurdle, as shown in Figure 3-5. If you think about varying complexity and size of many organizations' networks, you can get an appreciation for how difficult organizations may find enforcing NAC policies across their entire network.
Ultimately, the main policy server in your NAC implementation has to provide to the various network and endpoint elements specific instructions about what a particular end user is allowed to access on the network.
Figure 3.5. The enforcement of your NAC policies.
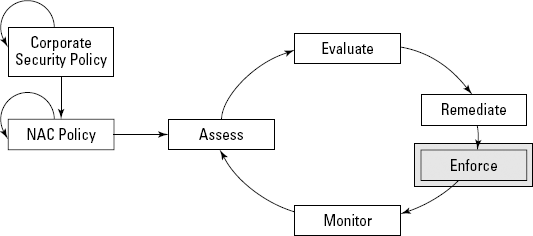
Most vendors' NAC solutions utilize one of three primary enforcement points:
Endpoint: Uses the pre-installed NAC agent software as a means of policing traffic and enforcing access control policies. ...
Get Network Access Control For Dummies® now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.


