26.6 THRESHOLD PATTERN MODELING
In the previous section, we have classified wireless sensor networks into three most network topologies based on the data delivery models. In this section, we propose the generation of threshold subpattern values for storage and comparison within the attack detector nodes based on these defined network topologies.
The analytical model of a sensor network undergoing a DDoS attack consists of two types of network traffic, namely, normal and attack. The flow of traffic in a typical sensor network is directed from the sensors to the base station. During normal operations mode, a sensor node may receive traffic from several sources, such as from nodes within its immediate vicinity. The volume of traffic and, in essence, the numbers of traffic flows are higher if the sensor node is a cluster-head or a data aggregation node. The traffic constituting a distributed denial of service attack can also be categorised as a flow, albeit with a different label. We assume that each adversarial node generates a single flow of traffic toward a victim node r. In the presence of attack traffic, the total traffic received by a target node r in a given time epoch, and that needs to be monitored by the attack detection scheme, is given by
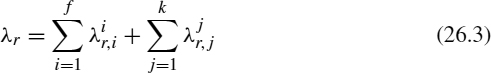
where ![]() is the normal traffic rate ...
is the normal traffic rate ...
Get Mobile Intelligence now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

