Analyzing the app using drozer
Drozer's inbuilt module app.package.manifest will give us presentable information about the AndroidManifest.xml file and display it in the console, as shown in the following screenshot:
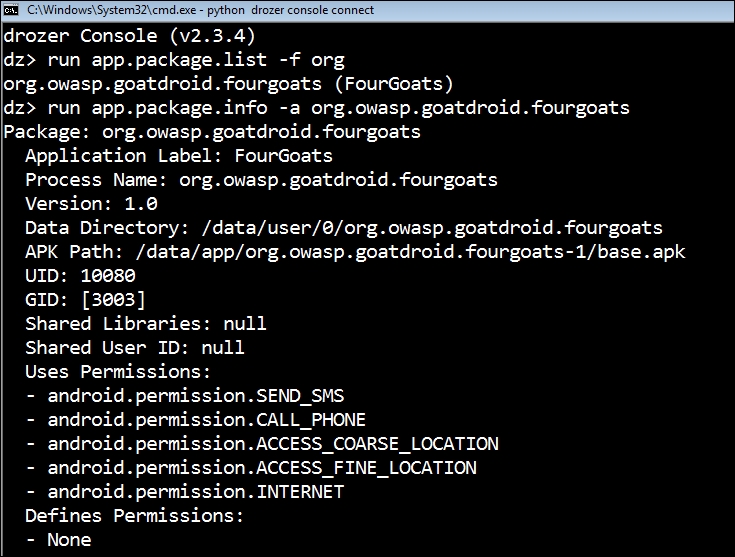
This output helps us understand the app's Process Name, Data Directory, APK Path, UID and GID, Shared Libraries and Shared User ID (if any), and most importantly, permission details.
Our target app, FourGoats, has permissions to send SMSes, make phone calls, and access location data and the Internet on the mobile device.
Note
These details can also be extracted using other tools, such as APKTOOL and Androguard.
Get Mobile Application Penetration Testing now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

