Exploring Audit Policies
A secure operating system needs to be able to identify individual users, grant access based on their identities, and track their actions. This starts by implementing practices that reflect the three As (AAA) of security: authentication, authorization, and accounting. Figure 5-1 shows how they combine to contribute to reliable accountability within an organization.
The AAAs of security refers to authentication, authorization, and accounting. Together they provide accountability.
Figure 5-1: AAA of security
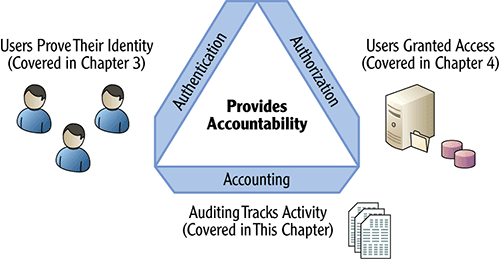
When a user attempts to access a system, the first step is to ensure that users prove who they are or authenticate ...
Get Microsoft® Windows® Security: Essentials now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

