Decryption Process
When a user requests a file that is encrypted, EFS locates the name of the encrypter in the DDF within the $Logged_Utility_Stream and uses that as a hint for finding the private key to decrypt the FEK. EFS uses a user's private key to decrypt the FEK, using the corresponding encrypted FEK item in the DDF. As shown in Figure 21.3, the FEK is used to decrypt the file data on a block-by-block basis.
Figure 21.3. EFS decryption flow chart.
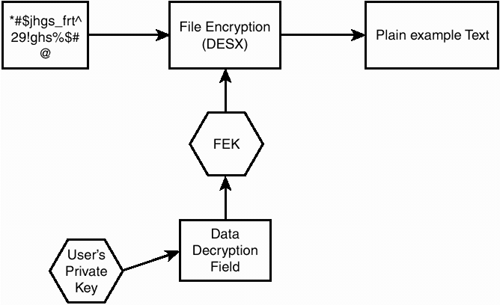
Random access to a large file decrypts only the specific blocks read from a disk for the file; EFS does not need to decrypt the entire file. EFS encrypts and decrypts by reading in 512-byte ...
Get Microsoft® Windows® 2000 Security Handbook now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

