Getting a Shell
At this point, the user has no new messages, so he decides to do some web browsing. When the browser opens, a captive portal is presented to the user, as shown in Figure 12-1.
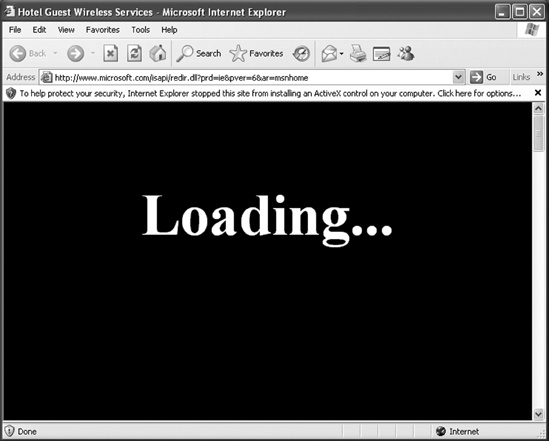
Figure 12-1. Karmetasploit captive portal
As the user sits in front of his computer wondering what’s going on, Karmetasploit is busy configuring the attack to capture cookies; set up fake email, DNS, and other servers; and launch exploits against the client’s browser—all the result of the magic contained in our karma.rc file.
Of course, some degree of luck is involved in this attack. The browser will display a “Loading” page while exploits are launched. If the ...
Get Metasploit now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

