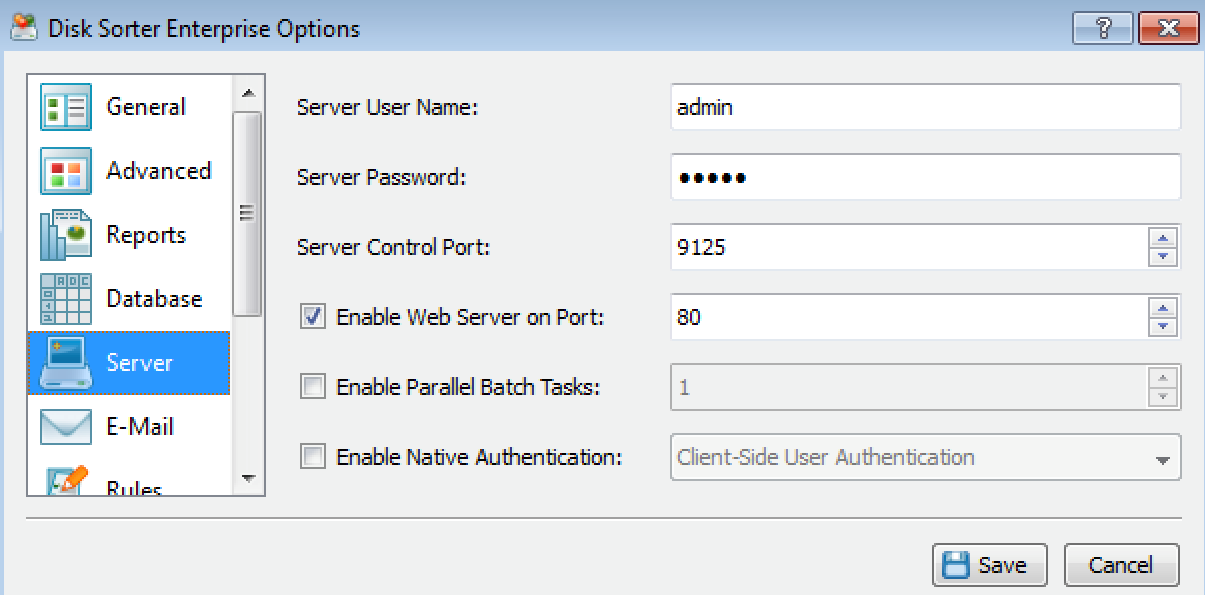
We will start by downloading a PoC I created a while back, which exploits a stack-based buffer overflow vulnerability in the web interface of Disk Sorter Enterprise v9.5.12, caused by improper bounds checking of the request path in HTTP GET requests sent to the built-in web server. The PoC and the vulnerable application are available in the Exploit Database website at https://www.exploit-db.com/exploits/41666/. To set up the vulnerable application, install it on the Windows 7 target machine then navigate to Tools | Disk Sorter Enterprise Options | Server and enable the web server on port 80 to start the web interface: