- We will start by using the Windows Gather Wireless Current Connection Info post-exploitation module to gather information about the current connection on each wireless LAN interface, on the target machine:

- Next, we can use the Windows Gather Wireless BSS Info post-exploitation module to gather information about the wireless basic service sets available to the victim machine:
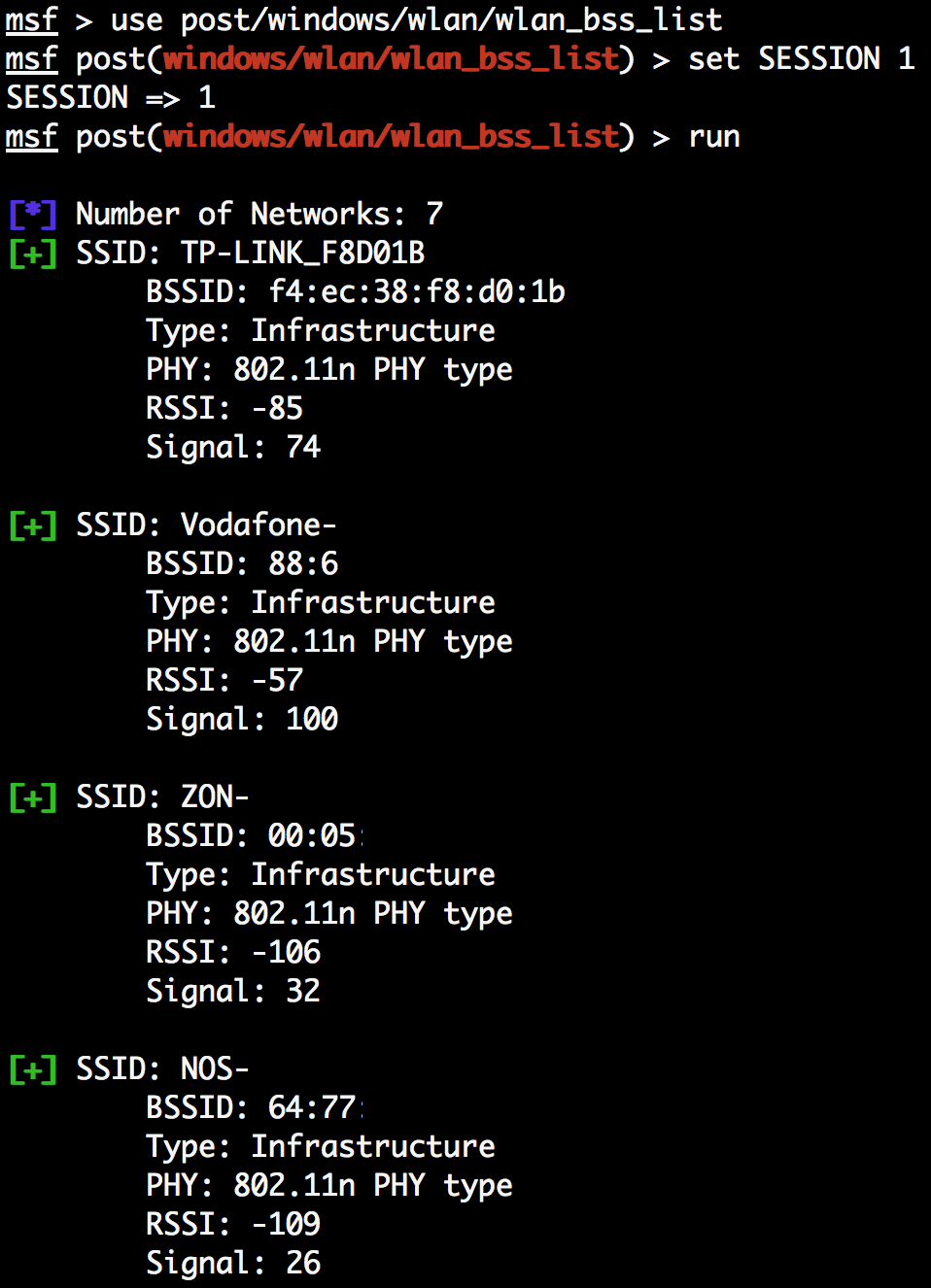
Using the output of this module we can, for example, use WiGLE, a website for collecting information about the different wireless hotspots around the ...

