Before we begin with the exploit conversion, it is important to learn how stack-based buffer overflows work.
A stack-based buffer overflow occurs when more data is written to a buffer than it can hold, overrunning the buffer's boundary and overwriting adjacent memory locations.
Looking at the PoC, we can see by sending 2487 characters we can overflow the next SEH and the SEH record:
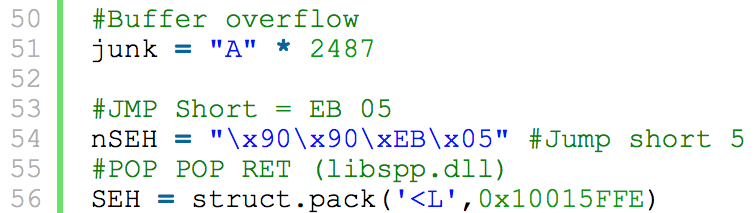
A Structured Exception Handler (SEH) is an exception handling mechanism. When a program crashes and an exception is triggered, SEH is called to try to recover operations. SEH is a linked list containing a sequence of data records; when an exception ...

