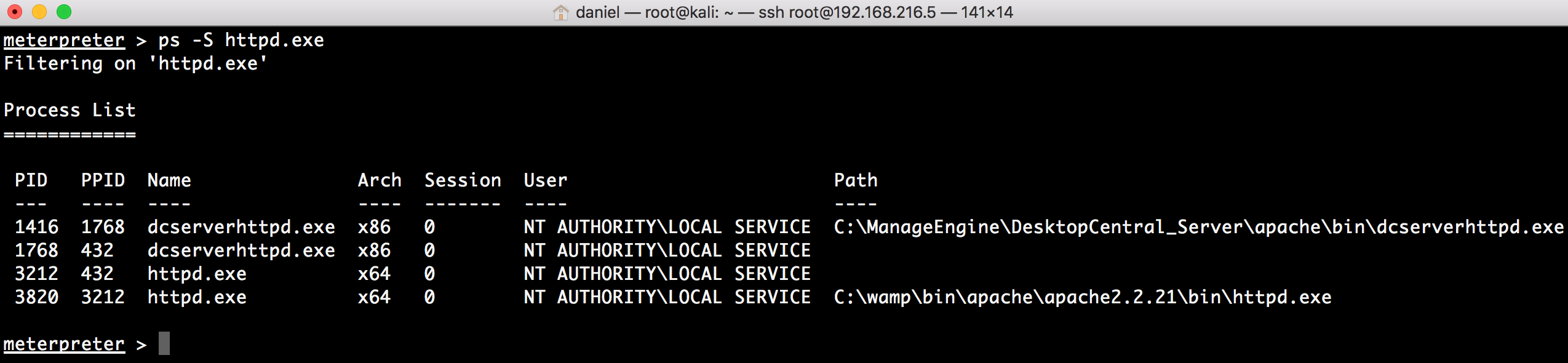
Now that we have a session in the target system, we will use that session to backdoor a service; in this recipe, we will start by backdooring the Apache server:
Next, we will use the Windows Registry Only Persistence local exploit module to create a backdoor that is executed during boot.
Lastly, we will use Windows Management Instrumentation (WMI) to create a persistent fileless backdoor. The WMI Event Subscription Persistence exploit module creates a permanent WMI event subscription to achieve file-less persistence.

