Exploiting CSRF in JSON requests
JSON is a popular format to exchange data over the Internet in client-server architectures. These days there's a growing trend in which developers are utilizing JSON for browser to server communication.
A JSON-based POST data looks like the following:
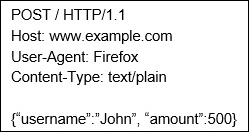
In terms of our CSRF exploitation scenario, the problem arises with the fact that there are no query parameters with the JSON format, which are a must with self-submitting forms. To bypass this, we can use a self-submitting form, with a hidden input with only a name attribute but no value. In other words, the name will contain the JSON payload to exploit the CSRF. We'll ...
Get Mastering Modern Web Penetration Testing now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

