Modeling threats
From the intelligence gathering phase, we can see that there are numerous services running on the target. Hosts information also reveals that the target operating system is Linux-based. Let us search for one of the vulnerabilities within Metasploit and try to find the matching exploit module:
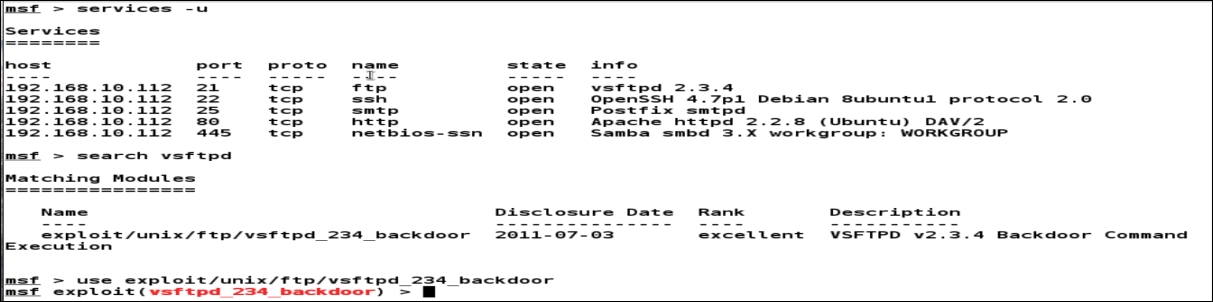
We can see that we already have a module in Metasploit that targets the vulnerable service found. After exploring the details at http://www.securityfocus.com/bid/48539/discuss and http://scarybeastsecurity.blogspot.in/2011/07/alert-vsftpd-download-backdoored.html, we can easily figure out that the vulnerability was intentionally put into the ...
Get Mastering Metasploit now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

