Providing additional features and further readings
SET is comprised of too many attacks, and covering them all here will push us beyond the scope of the book. However, some more information about attacks with SET can be found at http://www.social-engineer.org/framework/se-tools/computer-based/social-engineer-toolkit-set/.
SET can also be made to run against wireless vectors. More information on wireless attacks with SET can be found at http://resources.infosecinstitute.com/raising-a-rogue-access-point/.
The SET web interface
SET also provides a user-friendly web interface that is run by typing in the following command:
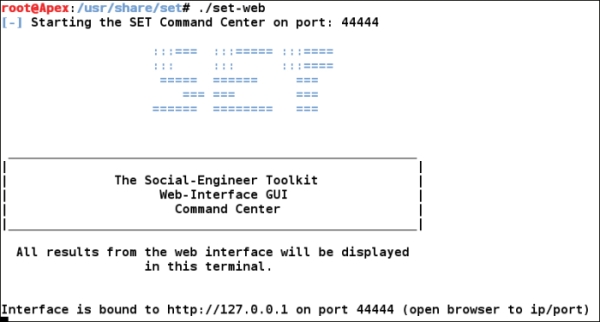
After the interface gets bound ...
Get Mastering Metasploit now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

