Let's see what services are running on the hosts in the target range by right-clicking on the desired host and clicking on Services. The results should look similar to the following screenshot:
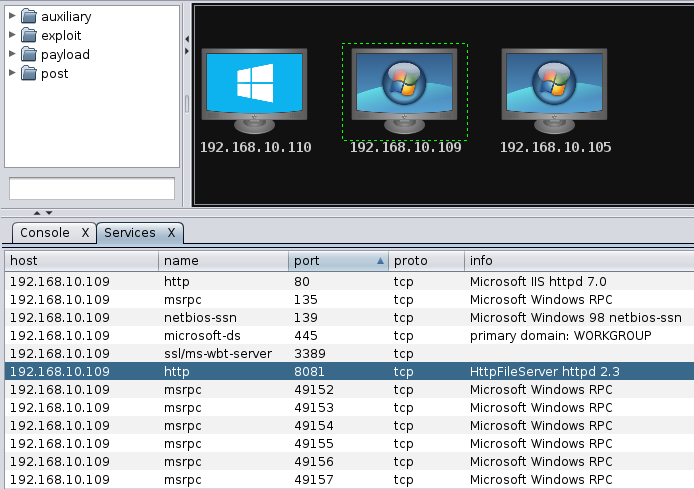
We can see many services running on the 192.168.10.109 host, such as Microsoft IIS httpd 7.0, Microsoft Windows RPC, HttpFileServer httpd 2.3, and much more. Let's target one of these services by instructing Armitage to find a matching exploit for these services.

