In the following section, we will see how we can import browser-based or TCP server-based exploits in Metasploit.
During an application test or a penetration test, we might encounter software that may fail to parse data from a request/response and end up crashing. Let's see an example of an application that has vulnerability when parsing data:
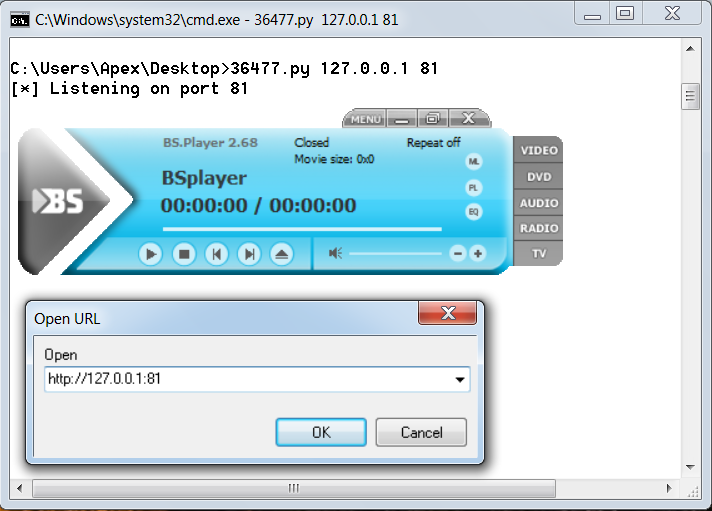
The application used in this example is BSplayer 2.68. We can see that we have a Python exploit listening on port 81. The vulnerability lies in parsing the remote server's response when a user tries to play a video from a URL. Let's see what ...

