Chapter 7. Authentication and User Management
Now that we have successfully installed Kubernetes, one of the most fundamental aspects of a successful deployment centers around consistent user management. As with any multitenant, distributed system, user management forms the basis for how Kubernetes ultimately authenticates identities, determines appropriate levels of access, enables self-service capabilities, and maintains auditability.
In this chapter and the next, we explore how to make the best use of the authentication and access control capabilities of Kubernetes. But to get a true understanding of how these constructs work, it is important to first understand the life cycle of an API request.
Every API request that makes its way to the API server needs to successfully navigate a series of challenges, as illustrated in Figure 7-1, before the server will accept (and subsequently act) on the request. Each of these tests falls into one of three groups: authentication, access control, and admission control.
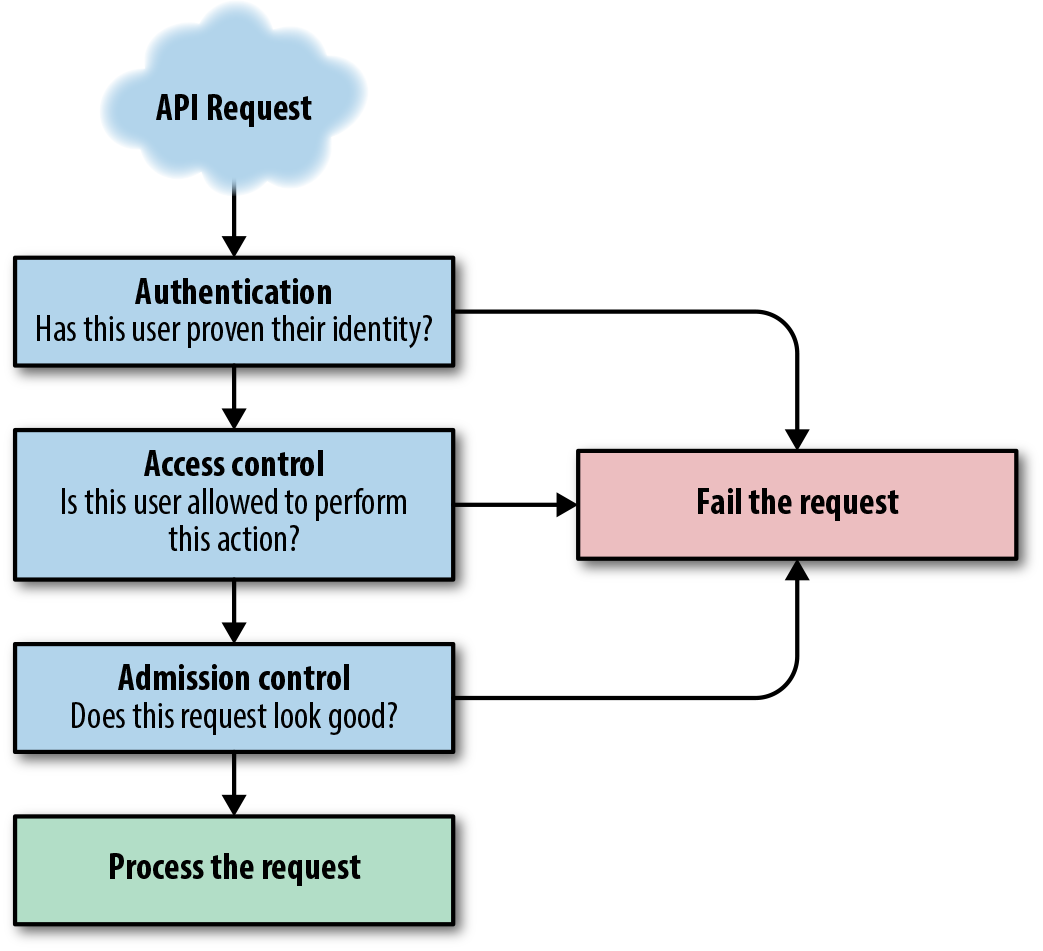
Figure 7-1. Kubernetes API request flow
The number and complexity of these challenges depends on how the Kubernetes API server is configured, but best practices call for production clusters to implement all three in some form or fashion.
The first two phases of servicing an API request (authentication and access control) focus on what we know about a user. In this chapter, ...
Get Managing Kubernetes now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

