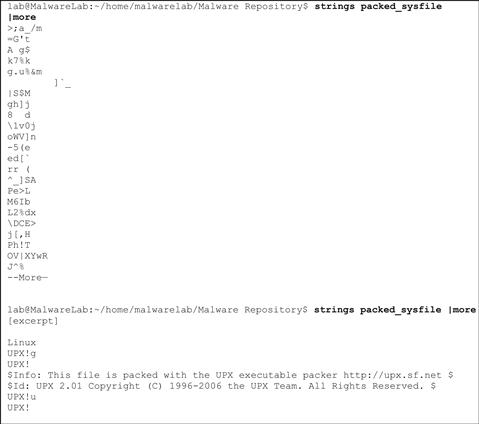
FIGURE 5.46 Extracting strings from a packed ELF executable
Embedded Artifact Extraction Revisited
☑ After successfully executing a malicious code specimen (Chapter 6), conducting process memory trajectory analysis (Chapter 6), or extracting the executable from physical memory (Chapter 3), re-examine the specimen for embedded artifacts.
▶ After successfully executing a malicious code specimen or extracting the executable from physical memory, re-examine the unobscured program for strings, symbolic information, file metadata, and ELF structural details. In this way, a comparison of the “before” and “after” file will reveal more clearly the ...
Get Malware Forensics Field Guide for Linux Systems now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

