3.7. Restricting Access by Remote Users
Problem
You want only particular remote users to have access to a TCP service. You cannot predict the originating hosts.
Solution
Block the service’s incoming TCP port with a firewall rule [Recipe 2.6], run an SSH server, and permit users to tunnel in via SSH port forwarding. Thus, SSH authentication will permit or deny access to the service. Give your remote users SSH access by public key.
For example, to reach the news server (TCP port 119) on your site server.example.com, a remote user on host myclient could consruct the following tunnel from (arbitrary) local port 23456 to the news server via SSH:
myclient$ ssh -f -N -L 23456:server.example.com:119 server.example.com
and then connect to the tunnel, for example with the tin newsreader:
myclient$ export NNTPSERVER=localhost myclient$ tin -r -p 23456
Discussion
SSH tunneling, or port forwarding, redirects a TCP connection to flow through an SSH client and server in a mostly-transparent manner.[1] [Recipe 6.14] This tunnel connects from a local port to a remote port, encrypting traffic on departure and decrypting on arrival. For example, to tunnel NNTP (Usenet news service, port 119), the newsreader talks to an SSH client, which forwards its data across the tunnel to the SSH server, which talks to the NNTP server, as in Figure 3-2.
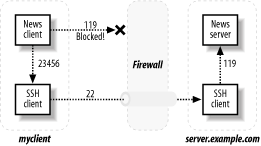
Figure 3-2. Tunneling NNTP with SSH
By blocking a service’s port (119) ...
Get Linux Security Cookbook now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

