Chapter 1. Introduction to Linux Networking
1.0. Introduction
Computer networking is all about making computers talk to each other. It is simple to say, but complex to implement. In this Introduction, we’ll take a bird’s-eye view of Ethernet networking with Linux, and take a look at the various pieces that make it all work: routers, firewalls, switches, cabling, interface hardware, and different types of WAN and Internet services.
A network, whether it is a LAN or WAN, can be thought of as having two parts: computers, and everything that goes between the computers. This book focuses on connectivity: firewalls, wireless access points, secure remote administration, remote helpdesk, remote access for users, virtual private networks, authentication, system and network monitoring, and the rapidly growing new world of Voice over IP services.
We’ll cover tasks like networking Linux and Unix boxes, integrating Windows hosts, routing, user identification and authentication, sharing an Internet connection, connecting branch offices, name services, wired and wireless connectivity, security, monitoring, and troubleshooting.
Connecting to the Internet
One of the biggest problems for the network administrator is connecting safely to the Internet. What sort of protection do you need? Do you need expensive commercial routers and firewalls? How do you physically connect your LAN to the Internet?
Here are the answers to the first two questions: at a minimum, you need a firewall and a router, and no, you do not need expensive commercial devices. Linux on ordinary PC hardware gives you all the power and flexibility you need for most home and business users.
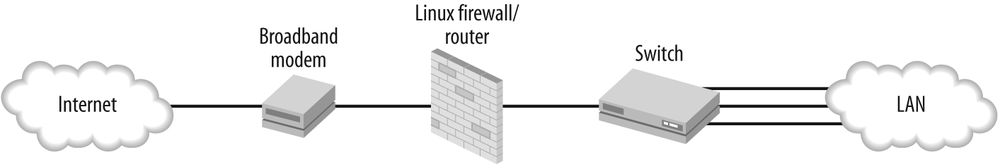
The answer to the last question depends on the type of Internet service. Cable and DSL are simple—a cable or DSL line connects to an inexpensive broadband modem, which you connect to your Linux firewall/gateway, which connects to your LAN switch, as Figure 1-1 shows.
In this introduction, I’m going to refer to the interface between your LAN and outside networks as the gateway. At a bare minimum, this gateway is a router. It might be a dedicated router that does nothing else. You might add a firewall. You might want other services like name services, a VPN portal, wireless access point, or remote administration. It is tempting to load it up with all manner of services simply because you can, but from security and ease-of-administration perspectives, it is best to keep your Internet gateway as simple as possible. Don’t load it up with web, mail, FTP, or authentication servers. Keep it lean, mean, and as locked-down as possible.
If you are thinking of upgrading to a high-bandwidth dedicated line, a T1 line is the next step up. Prices are competitive with business DSL, but you’ll need specialized interface hardware that costs a lot more than a DSL modem. Put a PCI T1 interface inside your Linux gateway box to get the most flexibility and control. These come in many configurations, such as multiple ports, and support data and voice protocols, so you can tailor it to suit your needs exactly.
If you prefer a commercial router, look for bundled deals from your service provider that include a router for free. If you can’t get a deal on a nice router, check out the abundant secondhand router market. Look for a router with a T1 WAN interface card and a Channel Service Unit/Data Service Unit (CSU/DSU). Don’t expect much from a low-end router—your Linux box with its own T1 interface has a lot more horsepower and customizability.
A typical T1 setup looks like Figure 1-2.
Beyond T1, the sky’s the limit on service options and pricing. Higher-end services require different types of hardware LAN interfaces. A good service provider will tell you what you need, and provide optional on-site services. Don’t be too proud to hire help—telecommunications is part engineering and part voodoo, especially because we started pushing data packets over voice lines.
Overview of Internet Service Options
The hardworking network administrator has a plethora of choices for Internet connectivity, if you are in the right location. A wise (though under-used) tactic is to investigate the available voice and data services when shopping for an office location. Moving into a space that is already wired for the services you want saves money and aggravation. Otherwise, you may find yourself stuck with nothing but dial-up or ISDN, or exotic, overpriced, over-provisioned services you don’t want.
Cable, DSL, and Dial-Up
Cable, DSL, and dial-up are unregulated services. These are the lowest-cost and most widely available.
Cable
Cable Internet is usually bundled with television services, though some providers offer Internet-only service. Cable’s primary attraction is delivering higher download speeds than DSL. Many providers do not allow running public services, and even block common ports like 22, 25, 80, and 110. Some vendors are notorious for unreliable service, with frequent outages and long downtimes. However, some cable providers are good and will treat you well, so don’t be shy about shopping around. Beware restrictive terms of service; some providers try to charge per-client LAN fees, which is as silly as charging per-user fees for tap water.
DSL
DSL providers are usually more business-friendly. Some DSL providers offer business DSL accounts with SLAs, and with bandwidth and uptime guarantees. DSL isn’t suitable for mission-critical services because it’s not quite reliable enough for these, but it’s fine for users who can tolerate occasional downtimes.
DSL runs over ordinary copper telephone lines, so anyone with a regular landline is a potential DSL customer. It is also possible to get a DSL line without telephone service, though this is usually expensive. DSL is limited by distance; you have to be within 18,000 wire-feet of a repeater, though this distance varies a lot between providers, and is affected by the physical quality of the line. Residential accounts are often restricted to shorter distances than business accounts, presumably to limit support costs.
With DSL, you’re probably stuck with a single telco, but you should have a choice of ISP.
DSL comes in two primary flavors: symmetric digital subscriber line (SDSL) and asymmetric digital subscriber line (ADSL). SDSL speeds are the same upstream and downstream, up to a maximum of 3 Mbps. ADSL downstream speeds go as high as 9 Mbps, but upstream maxes out at 896 Mbps. ADSL2+, the newest standard, can deliver 24 Mbps downstream, if you can find a provider. Keep in mind that no one ever achieves the full speeds; these are theoretical upper limits.
Longer distances means less bandwidth. If you’re within 5,000 feet you’re golden, assuming the telco’s wires are healthy. 10,000 is still good. The reliability limit of the connection is around 18,000 feet—just maintaining connectivity is iffy at this distance.
Dial-up
Good old dial-up networking still has its place, though its most obvious limitation is bandwidth. It’s unlikely you’ll get more than 48 Kbps. However, dial-up has its place as a backup when your broadband fails, and may be useful as a quick, cheap WAN—you can dial in directly to one of your remote servers, for example, and do a batch file transfer or some emergency system administration, or set it up as a VPN for your users.
Cable, DSL, and dial-up gotchas
One thing to watch out for is silly platform limitations—some ISPs, even in these modern times, are notorious for supporting only Microsoft Windows. Of course, for ace network administrators, this is just a trivial annoyance because we do not need their lackluster support for client-side issues. Still, you must make sure your Linux box can connect at all, as a significant number of ISPs still use Microsoft-only networking software. Exhibit A is AOL, which supports only Windows and Mac, and replaces the Windows networking stack with its own proprietary networking software. This causes no end of fun when you try to change to a different ISP—it won’t work until you reinstall Windows networking, which sometimes works, or reinstall Windows, which definitely works, and is almost as much fun as it sounds.
Regulated Broadband Services
Regulated services include broadband networking over copper telephone lines and fiber optic cable. These are supposed to be more reliable because the network operators are supposed to monitor the lines and fix connectivity problems without customer intervention. When there is a major service interruption, such as a widespread power outage, regulated services should be restored first. As always in the real world, it depends on the quality of your service provider.
T1, T3, E-1, E-3, DS1, and DS3 run over copper lines. T1/T3 and DS1/DS3 are the same things. These are symmetrical (same bandwidth upstream and downstream) dedicated lines. Because it’s an unshared line, even a T1 handles a lot of traffic satisfactorily. OC-3–OC-255 run over fiber optic cable; these are the super-high capacity lines that backbone providers use. Table 1-1 shows a sampling of the many available choices, including European standards (prefixed with an E).
Servicetype | Speed |
T1/DS1 | 1.544 Mbps |
T3/DS3 | 43.232 Mbps |
OC-3 | 155 Mbps |
OC-12 | 622 Mbps |
OC-48 | 2.5 Gbps |
OC-192 | 9.6 Gbps |
OC-255 | 13.21 Gbps |
E-1 | 2.048 Mbps |
E-2 | 8.448 Mbps |
E-3 | 34.368 Mbps |
Other common options are frame relay and fractional services, like fractional T1, fractional T3, and fractional OC-3. Frame relay is used point-to-point, for example, between two branch offices. It’s shared bandwidth, and used to be a way to save money when a dedicated T1 was too expensive. These days, it’s usually not priced low enough to make it worthwhile, and the hardware to interface with frame relay is expensive. DSL or T1 is usually a better deal.
Fractional T1 is still an option for users on a budget, though DSLis often a good lower-cost alternative. When you need more than a single T1, bonding two T1 lines costs less than the equivalent fractional T3 because the T3 interface hardware costs a mint. Linux can handle the bonding, if your interface hardware and service provider support it. When you think you need more than two T1s, it’s time to consult with your friendly service provider for your best options.
Always read the fine print, and make sure all fees are spelled out. The circuit itself is often a separate charge, and there may be setup fees. If you’re searching online for providers and information, beware of brokers. There are good ones, but as a general rule, you’re better off dealing directly with a service provider.
Private Networks
As more service providers lay their own fiber optic networks, you’ll find interesting options like Fast Ethernet WAN, even Gigabyte Ethernet WAN, and also high-speed wireless services. Again, these depend on being in the right location. The nice part about these private services is they bypass the Internet, which eliminates all sorts of potential trouble spots.
Latency, Bandwidth, and Throughput
When discussing network speeds, there is often confusion between bandwidth, latency, and throughput. Broadband means fat pipe, not necessarily a fast pipe. As us folks out here in the sticks say, “Bandwidth is capacity, and latency is response time. Bandwidth is the diameter of your irrigation line. Latency is waiting for the water to come out.”
Throughput is the amount of data transferred per unit of time, like 100 Kbps. So, you could say throughput is the intersection of bandwidth and latency.
Many factors affect latency, such as server speed, network congestion, and inherent limitations in circuits. The ping command can measure latency in transit time roundtrip:
$ ping oreilly.com
PING oreilly.com (208.201.239.37) 56(84) bytes of data.
64 bytes from www.oreillynet.com (208.201.239.37): icmp_seq=2 ttl=45 time=489 ms
64 bytes from www.oreillynet.com (208.201.239.37): icmp_seq=3 ttl=45 time=116 msCompare this to LAN speeds:
$ ping windbag
PING localhost.localdomain (127.0.0.1) 56(84) bytes of data.
64 bytes from localhost.localdomain (127.0.0.1): icmp_seq=1 ttl=64 time=0.040 ms
64 bytes from localhost.localdomain (127.0.0.1): icmp_seq=2 ttl=64 time=0.039 msIt doesn’t get any faster than pinging localhost. The latency in an Ethernet interface is around 0.3 milliseconds (ms). DSLand cable are around 20 ms. T1/T3 have a latency of about 4 ms. Satellite is the highest, as much as two seconds. That much latency breaks IP. Satellite providers play a lot of fancy proxying tricks to get latency down to a workable level.
Hardware Options for Your Linux Firewall/Gateway
There are a lot of hardware choices for your gateway box. Linux supports more hardware platforms than any other operating system, so you don’t have to stick with x86. Debian in particular supports a large number of hardware architectures: Alpha, ARM, HPPA, i386, ia64, m68k, MIPS, MIPSEL, PowerPC, SPARC, and s/390, so you can use whatever you like. (If you build one on an s/390, please send photos to carla@bratgrrl.com!)
Of course, you have the option of purchasing a commercial appliance. These range from little SOHO devices like the Linksys, Netgear, and SMC broadband routers for sharing a DSL or cable Internet line for under $100, to rackmount units that end up costing several thousand dollars for software licenses and subscriptions. A growing number of these are Linux-based, so your Linux skills will serve you well.
But, it’s not necessary to go this route—you can get unlimited flexibility, and possibly save money by purchasing the bare hardware, or reusing old hardware, and installing your own favorite Linux distribution on it.
There are many choices for form factor and hardware types: small embedded boards like Soekris and PC Engines, Mini-ITX, microATX, blade, rackmount, and more. The smaller units use less power, take up less space, and are fanless for peace and quiet. Larger devices are more configurable and handle bigger loads.
A plain old desktop PC makes a perfectly good gateway box, and is a good way to keep obsolete PCs out of landfills. Even old 486s can do the job for up to a hundred or so users if they are just sharing an Internet connection and not running public services. Repurposed PCs may be a bit questionable for reliability just from being old, and you may not be able to get replacement parts, so if you’re nervous about their reliability, they still work great for training and testing. An excellent use for one of these is as a fully provisioned backup box—if your main one fails, plug in the backup for minimal downtime.
High-End Enterprise Routers
When do you need an elite, hideously expensive, top-of-the-line Cisco or Juniper router? To quote networking guru Ed Sawicki: “You don’t need more performance than what you need.” Unless you’re an ISP handling multimegabyte routing tables, need the fastest possible performance, highest throughput, good vendor support, and highest reliability, you don’t need these superpowered beasts.
The highest-end routers use specialized hardware. They are designed to move the maximum number of packets per second. They have more and fatter data buses, multiple CPUs, and TCAM memory.
TCAM is Ternary Content Addressable Memory. This is very different from ordinary system RAM. TCAM is several times faster than the fastest system RAM, and many times more expensive. You won’t find TCAM in lower-cost devices, nor will you find software that can shovel packets as fast as TCAM.
Not-So-High-End Commercial Routers
The mid-range commercial routers use hardware comparable to ordinary PC hardware. However, their operating systems can make a significant performance difference. Routers that use a real-time operating system, like the Cisco IOS, perform better under heavy loads than Linux-based routers, because no matter how hard some folks try to make Linux a real-time operating system, it isn’t one.
But, for the average business user this is not an issue because you have an ISP to do the heavy lifting. Your needs are sharing your Internet connection, splitting a T1 line for voice and data, connecting to some branch offices, offsite backups, or a data center. Linux on commodity hardware will handle these jobs just fine for a fraction of the cost.
Switches
Switches are the workhorses of networking. Collision domains are so last millennium; a cheap way to instantly improve LAN performance is to replace any lingering hubs with switches. Once you do this, you have a switched LAN. As fiber optic lines are becoming more common, look for cabling compatibility in switches. (And routers and NICs, too.)
Switches come in many flavors: dumb switches that simply move packets, smart switches, and managed switches. These are marketing terms, and therefore imprecise, but usually, smart switches are managed switches with fewer features and lower price tags. Higher-end features have a way of falling into lower-priced devices over time, so it no longer costs a scary amount to buy managed or smart switches with useful feature sets. There are all kinds of features getting crammed into switches these days, so here is a list of some that I think are good to have.
Management port
Because switches forward traffic directly to the intended hosts, instead of promiscuously spewing them to anyone who cares to capture them, you can’t sniff a switched network from anywhere on a subnet like you could in the olden hub days. So, you need a switch that supports port mirroring, or, as Cisco calls it, SPAN. (An alternative is to use the arpspoof utility—use it carefully!)
Serial port
Most managed switches are configured via Ethernet with nice web interfaces. This is good. But still, there may be times when you want to get to a command line or do some troubleshooting, and this is when a serial port will save the day.
MDI/MDI-X (Medium Dependent Interfaces)
This is pretty much standard—it means no more hassles with crossover cables, because now switches can auto-magically connect to other switches without needing special uplink ports or the exactly correct crossover or straight-through cables.
Lots of blinky lights
Full banks of LEDs can’t be beat for giving a fast picture of whether things are working.
Jumbo frames
This is a nice feature on gigabit switches, if it is supported across your network. Standard frames are 1,500 bytes, which is fine for Fast Ethernet. Some Gigabit devices support 9,000 byte frames.
Port trunking
This means combining several switch ports to create a fatter pipeline. You can connect a switch to a switch, or a switch to a server if it has a NIC that supports link aggregation.
VLANs
This is a feature that will have you wondering why you didn’t use it sooner. Virtual LANs (VLANs) are logical subnets. They make it easy and flexible to organize your LAN logically, instead of having to rearrange hardware.
QoS
Quality of Service, or traffic prioritization, allows you to give high priority to traffic that requires low latency and high throughput (e.g., voice traffic), and low priority to web-surfin’ slackers.
Per-port access controls
Another tool to help prevent intruders and snoopy personnel from wandering into places they don’t belong.
Network Interface Cards (NICs)
With Linux, it’s unlikely you’ll run into driver hassles with PCI and PCI-Express NICs; most chipsets are well-supported. New motherboards commonly have 10/ 100/1000 Ethernet onboard. Just like everything else, NICs are getting crammed with nice features, like wake-on-LAN, netboot, QoS, and jumbo frame support.
USB NICs, both wired and wireless, are good for laptops, or when you don’t feel like opening the box to install a PCI card. But beware driver hassles; a lot of them don’t have Linux drivers.
Server NICs come with nice features like link aggregation, multiple ports, and fiber Gigabit.
Gigabit Ethernet Gotchas
As Gigabit Ethernet becomes more common, it’s important to recognize the potential choke points in your network. Now we’re at the point where networking gear has outstripped PC capabilities, like hard drive speeds, I/O, and especially bus speeds.
The PCI bus is a shared bus, so more devices result in slower performance. Table 1-2 shows how PCI has evolved.
PCI-Express is different from the old PCI, and will probably replace both PCI and AGP. It is backward-compatible, so you won’t have to chuck all of your old stuff. PCI-E uses a point-to-point switching connection, instead of a shared bus. Devices talk directly to each other over a dedicated circuit. A device that needs more band-width gets more circuits, so you’ll see slots of different sizes on motherboards, like PCI-Express 2x, 4x, 8x, and 16x. PCI-E x16 can theoretically move 8 Gbps.
USB 1.1 tops out at 11 Mbps, and you’ll be lucky to get more than 6–8 Mbps. USB 2.0 is rated at 480 Mbps, which is fine for both Fast and Gigabit wired Ethernet. You won’t get full Gigabit speeds, but it will still be faster than Fast Ethernet.
32-bit Cardbus adapters give better performance on laptops than the old 16-bit PCMCIA, with a data transfer speed of up to 132 Mbps.
Cabling
Ordinary four-twisted-pair Cat5 should carry you into Gigabit Ethernet comfortably, though Cat5e is better. Chances are your Cat5 is really Cat5e, anyway; read the cable markings to find out. Watch out for cheapie Cat5 that has only two twisted pairs.
Cat6 twisted-pair cabling, the next generation of Ethernet cabling, is a heavier gauge (23 instead of Cat5’s 24), meets more stringent specifications for crosstalk and noise, and it always has four pairs of wires.
Wireless Networking
Wireless networking gear continues to be a source of aggravation for admins of mixed LANs, which is practically all of them. Shop carefully, because a lot of devices are unnecessarily Windows-dependent. Wireless gear is going to be a moving target for awhile, and bleeding-edge uncomfortable. Go for reliability and security over promises of raw blazing speeds. As far as security goes, Wired Equivalent Privacy (WEP) is not suitable for the enterprise. WEP is far too weak. Wi-Fi Protected Access (WPA) implementations are all over the map, but WPA2 seems to be fairly sane, so when you purchase wireless gear, make sure it supports WPA2. Also, make sure it is Wi-Fi Certified, as this ensures interoperability between different brands.
Whatever you do, don’t run naked unprotected wireless. Unless you enjoy having your network compromised.
Get Linux Networking Cookbook now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.