Implementing a Basic Firewall
Sometimes you may want a host to provide certain services to only local clients or clients on other hosts of a network that you control. If your network is connected to the Internet, you can use a firewall to prevent undesired access to services. A Linux firewall depends on certain kernel facilities to examine incoming and outgoing packets. Packets that fail to pass specified rules can be rejected, preventing undesired access to private services. Unlike TCP Wrappers, a firewall does not require special support from applications or services it protects. And, a firewall can work with protocols other than TCP, such as UDP and ICMP.
Configuring the Firewall
To configure a firewall, launch the Security Level Tool by choosing System Settings → Security Level from the main menu.
The Security Level Tool (Figure 11-17) appears.
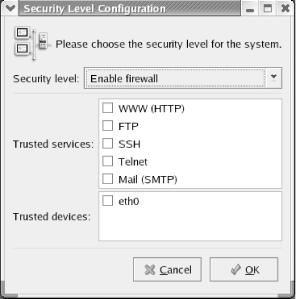
Figure 11-17. The Security Level Configuration dialog box
The Security Level Configuration dialog box lets you enable or disable the firewall. In addition, you can specify that requests for any of several predefined services are allowed to freely transit the firewall. To do so, simple enable the checkbox associated with the name of the service.
Tip
By allowing service requests to transit the firewall, you may expose your system to network-based attacks. Therefore, don’t specify trusted services casually or unnecessarily.
You can use the Trusted ...
Get Learning Red Hat Enterprise Linux & Fedora, Fourth Edition now with the O’Reilly learning platform.
O’Reilly members experience books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.

