The System Service Descriptor Table (SSDT) in kernel space contains the pointers to the system service routines (kernel functions) exported by the kernel executive (ntoskrnl.exe, ntkrnlpa.exe and so on). When an application calls an API such as WriteFile(), ReadFile(), or CreateProcess(), it calls the stub in the ntdll.dll which switches the thread to the kernel mode. The thread running in the kernel mode consults the SSDT to determine the address of the kernel function to invoke. The following screenshot illustrates this concept with an example of WriteFile() (the concept is similar for other APIs):
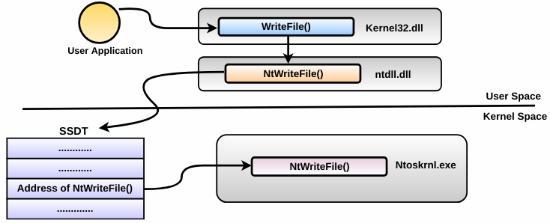
In general, ...

